GRC in cybersecurity stands for Governance, Risk, and Compliance. This strategic framework helps organizations align IT with business goals, manage cyber risks, and meet regulatory requirements without compromising security or efficiency.
Let’s cut through the corporate fluff. What is GRC in cybersecurity? It’s not just a buzzword tossed around by consultants in overpriced suits.
At its core, GRC, short for Governance, Risk, and Compliance, is the backbone of any serious security program.
It’s the system that defines how your organization makes security decisions, identifies threats, and avoids legal trouble.
And in today’s high-stakes digital environment, getting it wrong isn’t just risky, it’s catastrophic.
Whether you’re a CISO, sysadmin, or just someone who doesn’t trust checkboxes to keep hackers out, this guide will walk you through GRC without the B.S.
What Is GRC in Cybersecurity?
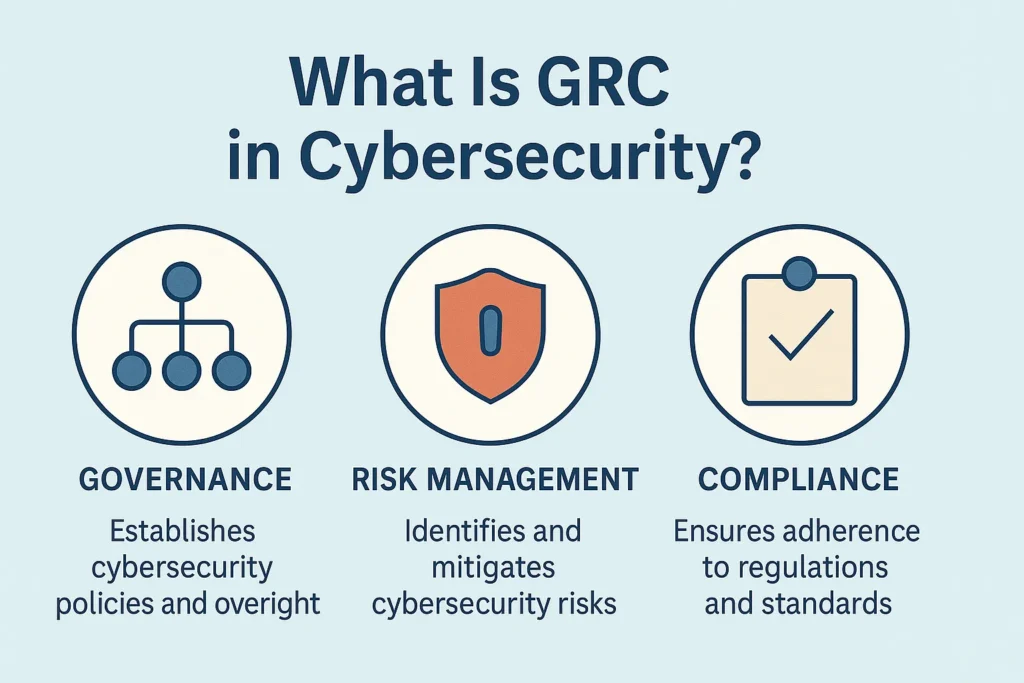
GRC in cybersecurity isn’t just a corporate buzzword; it’s a critical triad for building secure, resilient, and legally defensible systems.
Governance, Risk Management, and Compliance (GRC) form an integrated strategy that allows organizations to align cybersecurity initiatives with business goals, proactively manage risk, and meet stringent regulatory requirements.
Governance: Establishing Control and Accountability
Governance defines the structure and oversight of cybersecurity within an organization. It involves setting clear security policies, defining roles and responsibilities, and ensuring executive-level alignment with cybersecurity objectives. Governance answers key questions like:
- Who is responsible for enforcing security policies?
- How are decisions made about data protection and incident response?
- Are cybersecurity goals aligned with broader organizational strategy?
Effective governance requires visibility across the tech stack, strong leadership buy-in, and a culture of accountability; without it, the rest of GRC crumbles.
Read More On: Do You Need a Degree for Cybersecurity in 2025?
Risk Management: The Core of Cyber Defense
Risk management is where theory meets practice. It involves identifying digital assets, assessing vulnerabilities and threat vectors, estimating the likelihood and impact of potential attacks, and prioritizing mitigation efforts accordingly.
The goal isn’t to eliminate all risks (impossible), but to make informed decisions that balance security and operational needs.
Technically, this includes:
- Conducting risk assessments and penetration testing
- Implementing threat modeling methodologies like STRIDE or DREAD
- Using risk registers and metrics to track and communicate risk exposure
- Integrating with SIEM tools for continuous threat detection
Compliance: Meeting Legal and Industry Standards
Compliance ensures organizations meet the legal, regulatory, and contractual obligations tied to cybersecurity. This includes frameworks like:
- GDPR (data privacy)
- HIPAA (healthcare data security)
- NIST 800-53, ISO/IEC 27001 (information security management)
- SOX, PCI DSS, and others, depending on the industry
It also involves maintaining audit trails, conducting periodic assessments, and ensuring that security controls are both documented and enforced.
But compliance should be seen as a baseline, not the goal; true security requires going beyond what the law mandates.
Read More On: Will Cybersecurity Be Replaced By AI?
Why GRC in Cybersecurity Matters?

Cybersecurity threats are no longer just technical; they’re legal, financial, and reputational. GRC provides the scaffolding to manage this complexity. It enables organizations to:
- Avoid costly fines and legal consequences
- Detect and respond to threats faster.
- Build trust with users, partners, and regulators.
- Enable secure digital transformation.
In essence, GRC in cybersecurity bridges the gap between technical defense and organizational resilience, turning cybersecurity from a siloed IT function into a strategic business asset.
Read More On: How Do Macros Pose A Cybersecurity Risk?
Why GRC Is Critical in Today’s Threat Landscape?
Modern cybersecurity threats are faster, smarter, and more persistent than ever before. From zero-day exploits and deepfake phishing to ransomware cartels operating like Fortune 500 companies, defending digital assets now requires more than technical tools; it demands strategic coordination. This is where GRC becomes essential. Here’s how:
- Governance aligns security with business objectives
Cybersecurity isn’t just an IT issue, it’s a boardroom priority. Governance ensures that security policies, roles, and responsibilities are clearly defined and mapped to organizational goals. It provides:
- Executive visibility into cybersecurity posture
- Policy enforcement across departments
- A structure for making informed, accountable decisions
- Executive visibility into cybersecurity posture
- Risk management turns chaos into calculated action.
The modern threat landscape generates a flood of alerts, vulnerabilities, and unknowns. Risk management frameworks help prioritize and mitigate the most critical issues by:
- Identifying digital assets and attack surfaces
- Assessing vulnerabilities and threat vectors
- Applying quantitative models (like FAIR) to estimate risk exposure
- Focusing efforts where impact is highest and likelihood is real
- Identifying digital assets and attack surfaces
- Compliance safeguards against legal and reputational fallout
Regulatory frameworks are tightening globally. GDPR, HIPAA, PCI DSS, DORA, and CCPA are just the beginning. A solid compliance program helps:
- Ensure adherence to industry and legal standards.
- Maintain auditable records and control.s
- Automate checks and balances through continuous monitoring
- Reduce the risk of fines, lawsuits, and operational shutdown.s
- Ensure adherence to industry and legal standards.
- Threats evolve daily. GRC helps you evolve with them
Static defenses break under dynamic pressure. GRC frameworks are designed to be adaptive:
- Policies can be updated based on threat intelligence.ce
- Risk assessments can be continuous, not quarterly.
- Compliance requirements can be mapped across frameworks using unified tools.
- Policies can be updated based on threat intelligence.ce
- GRC integrates fragmented security tools into a coherent system
Most organizations suffer from tool sprawl, overlapping platforms that don’t talk to each other. GRC platforms help integrate:
- SIEM and SOAR systems for real-time monitoring and automated response
- Asset and vulnerability management tools for risk scoring
- Workflow automation for policy enforcement and compliance checks
- SIEM and SOAR systems for real-time monitoring and automated response
- Reputation is a target that GRC helps protect.
Customers, partners, and regulators are watching. A single breach can obliterate trust. GRC helps prove due diligence:
- Demonstrates proactive risk management
- Document policies, training, and incident response
- Builds confidence in your security program
- Demonstrates proactive risk management
Read More On: Does Cybersecurity Require Coding?
Core Components of a Cybersecurity GRC Program
A cybersecurity GRC program is more than just a compliance initiative. It’s the framework that binds policy, technology, and operational discipline into a single, coordinated defense strategy.
In a landscape where threats are constant and regulations are multiplying, a well-structured GRC program ensures that an organization can manage risk, enforce accountability, and prove security readiness at any moment.
Below are the core components that make such a program effective and sustainable.
1. Governance Structure
Governance is the foundation of a cybersecurity GRC program. It defines how security is managed across the organization, who is responsible for what, and how decisions are made.
Without strong governance, cybersecurity efforts often become fragmented, reactive, and misaligned with business priorities. A well-designed governance structure ensures that cybersecurity is not just a technical function but a business-critical discipline supported at every level.
Key elements of an effective governance structure include:
- Policies and Standards: These are the formal rules that guide behavior, access, data handling, and system usage. They should be aligned with established security frameworks and tailored to the organization’s specific risk profile.
- Roles and Responsibilities: Governance assigns ownership to key security roles such as CISO, risk managers, compliance officers, and business unit leaders. This ensures accountability and makes it clear who is responsible for implementation and oversight.
- Strategic Alignment: Governance connects security goals to business objectives. This means cybersecurity investments and actions are driven by what matters most to the organization, whether it’s protecting IP, ensuring uptime, or maintaining regulatory compliance.
- Security Committees and Oversight Bodies: These internal groups, often involving leadership from IT, legal, risk, and executive teams, meet regularly to review policies, analyze emerging risks, and approve strategic changes.
This structure ensures that decisions are made with clarity and purpose, and that cybersecurity is seen not just as a cost center but as a critical enabler of business continuity and trust.
Use Cybersecurity Risk Calculator
2. Risk Management Framework
While governance sets the rules and structure, risk management is about understanding what can go wrong and how to deal with it before it does. In a cybersecurity context, this means identifying threats, vulnerabilities, and the potential impact of incidents, then prioritizing which risks to address based on real-world context and consequences.
An effective risk management framework helps organizations avoid wasting time and money chasing every threat equally. Instead, it provides a methodical approach to focus on what’s truly critical. This involves continuous monitoring, business-aligned risk scoring, and proactive mitigation.
Key components include:
- Asset Inventory: Knowing what you’re protecting is step one. This includes hardware, software, data repositories, cloud services, and any digital endpoint that could be targeted.
- Threat and Vulnerability Assessment: Regular use of tools like vulnerability scanners, threat modeling frameworks (e.g., STRIDE or MITRE ATT&CK), penetration testing, and red teaming to identify security gaps.
- Risk Quantification: Moving beyond vague risk ratings by using models like FAIR to assign dollar values or operational impact estimates to risk scenarios. This helps security leaders speak the language of the business.
- Risk Register: A living document or platform that tracks known risks, their severity, assigned owners, mitigation plans, deadlines, and current status. It’s the source of truth for security posture.
This framework helps turn reactive firefighting into proactive risk management, allowing teams to anticipate threats instead of just responding to them.
3. Compliance and Regulatory Mapping
In today’s regulatory minefield, compliance is no longer optional. Whether it’s GDPR, HIPAA, PCI DSS, SOX, or DORA, every organization faces a growing list of legal and industry mandates that govern how data is handled, stored, and protected. Failing to meet these standards can result in heavy fines, lawsuits, and loss of reputation.
But compliance isn’t just about ticking boxes. When properly integrated into a GRC program, it becomes a force multiplier standardizing security practices, improving audit readiness, and proving to stakeholders that the organization takes data protection seriously.
A mature compliance function includes:
- Framework Alignment: Mapping internal security policies and controls to external regulatory standards. This ensures consistency and helps avoid duplication of effort across different frameworks.
- Audit Preparation and Management: Maintaining structured documentation, logs, and control evidence that can be easily retrieved for internal or third-party audits. This reduces audit fatigue and improves response times.
- Exception Management: No environment is perfect. When controls can’t be implemented as required, there must be a documented and approved exception process to manage and mitigate those gaps.
- Continuous Monitoring: Manual checklists don’t scale. Compliance tools should integrate with cloud platforms, SIEMs, and endpoint systems to automatically validate control status and alert on deviations in real time.
By embedding compliance into day-to-day operations, organizations can avoid last-minute scrambles and build trust with regulators, partners, and customers alike.
Read More On: Top 10 Cybersecurity Forensic Tools For Ethical Hackers In 2025
4. Incident Response and Continuity Planning
Even with the best defenses, breaches happen. What separates resilient organizations from victims is their ability to respond with speed, coordination, and clarity. That’s where incident response and business continuity planning come into play.
This component ensures that when a cyber incident occurs, whether it’s ransomware, data theft, or system failure, the organization has a structured, pre-approved plan to contain the damage, recover operations, and communicate effectively with all stakeholders.
Key parts of this component include:
- Incident Response Playbooks: Predefined procedures for specific scenarios such as malware outbreaks, phishing campaigns, insider threats, or denial-of-service attacks. These playbooks outline who does what, when, and how.
- Notification Protocols: Every minute counts during an incident. Clear, tested communication plans ensure that legal teams, executives, customers, and regulators are informed without delays or confusion.
- Disaster Recovery Plans (DRP): Technical blueprints for restoring systems, applications, and data after a disruption. This includes backup strategies, failover mechanisms, and recovery point objectives (RPOs) and recovery time objectives (RTOs).
- Business Continuity Procedures (BCP): Broader than DRP, these plans ensure critical business functions can continue during and after an incident. This could involve manual workarounds, remote work capabilities, or alternative suppliers.
Integrating these plans into the GRC program ensures that they are tested, regularly updated, and aligned with the organization’s risk appetite and operational priorities. It’s not just about surviving the breach, it’s about recovering smarter and faster than the adversary expects.
Read More On: Which Of The Following Activities Poses The Greatest Personal Cybersecurity Risk?
5. Security Awareness and Training
Technology can’t compensate for human error. Phishing, weak passwords, and social engineering remain some of the most effective attack vectors not because systems fail, but because people do.
That’s why a strong GRC program must include a dedicated focus on security awareness and training.
This component ensures that everyone in the organization, from the front desk to the C-suite, understands their role in protecting digital assets. It’s about turning employees from weak links into active defenders.
Key elements include:
- Training Programs: Role-based security training tailored to different functions. Developers need secure coding guidance, while HR needs to understand data privacy laws. Training should be recurring, engaging, and updated regularly.
- Simulated Attacks: Phishing simulations, USB baiting tests, and other ethical attack exercises help assess employee readiness and identify areas for improvement without real-world consequences.
- Policy Acknowledgment: Employees should formally acknowledge that they’ve read and understood core security policies. This not only reinforces accountability but also serves as legal evidence in the event of a breach.
- Behavioral Monitoring: Advanced programs track behavioral patterns to flag risky actions, such as repeated failed login attempts or unauthorized access attempts, and provide targeted interventions.
When integrated into a GRC framework, security awareness training becomes a measurable, reportable element of organizational risk posture, not just an annual checkbox.
6. Technology Integration and Automation
No GRC program can scale without smart integration. Today’s cybersecurity environment is a complex mesh of tools, platforms, and data streams.
Without automation and system-level integration, GRC quickly becomes a bureaucratic bottleneck instead of an operational force multiplier.
This component focuses on embedding GRC into the technology stack to streamline workflows, improve accuracy, and accelerate response.
Key elements include:
- Centralized GRC Platforms: Platforms like ServiceNow GRC, RSA Archer, or Drata provide a unified interface for managing governance, tracking risk, and ensuring compliance. These systems allow for cross-mapping of controls, real-time alerts, and automated reporting.
- Security Tool Integration: GRC tools should plug into your SIEM (for log data), SOAR (for incident automation), vulnerability management tools (for risk scoring), and asset inventory systems (for context). This enables real-time decision-making and eliminates data silos.
- Workflow Automation: Repetitive tasks like control assessments, evidence collection, policy reminders, and audit logging can be automated. This reduces human error and frees up time for higher-value work.
- Dashboards and Reporting: Real-time dashboards give security leaders and executives visibility into compliance gaps, risk trends, and incident statuses. These can be customized by audience; what a CISO needs to see is very different from what the board wants.
By integrating and automating wherever possible, a GRC program becomes more agile, scalable, and effective, turning compliance from a burden into a continuous, data-driven process.
7. Metrics and Continuous Improvement
A cybersecurity GRC program is only as strong as its ability to adapt. Threats evolve, business models shift, and regulations change. Without a continuous improvement loop, even a well-designed GRC system will become obsolete. That’s why measurement and feedback mechanisms are essential.
This component ensures the GRC program remains relevant, efficient, and aligned with the organization’s risk appetite and business strategy.
Key elements include:
- Key Risk Indicators (KRIs): These metrics highlight potential trouble spots before they explode. Examples include the number of unpatched critical vulnerabilities, failed login attempts, or changes in vendor risk ratings.
- Key Performance Indicators (KPIs): These measure the efficiency and effectiveness of the GRC program itself. Think of metrics like time-to-remediate, audit pass rates, incident response time, or training completion rates.
- Trend Analysis: Looking at metrics over time reveals patterns that drive better decisions. Are phishing click rates going down? Is third-party risk increasing? Trend data helps focus attention where it’s needed most.
- Lessons Learned: After every incident, audit, or failed control, there should be a debrief. What went wrong? What can be improved? These insights feed directly into policy updates, training programs, and control design.
- Policy and Control Reviews: GRC is not a “set it and forget it” function. Regular reviews ensure policies remain aligned with the threat landscape, legal requirements, and organizational changes.
By embedding metrics and feedback loops into the heart of the GRC program, organizations can stay ahead of threats, improve compliance efficiency, and demonstrate ongoing commitment to cybersecurity excellence.
Popular GRC Frameworks and Tools
Implementing GRC in cybersecurity is as much about choosing the right framework as it is about using the right tools. Frameworks provide the structure on what to do and how to align with best practices. Tools make it operational to track, enforce, and automate those practices at scale.
Here’s a breakdown of the most widely adopted frameworks and tools used in modern cybersecurity GRC programs:
Popular GRC Frameworks
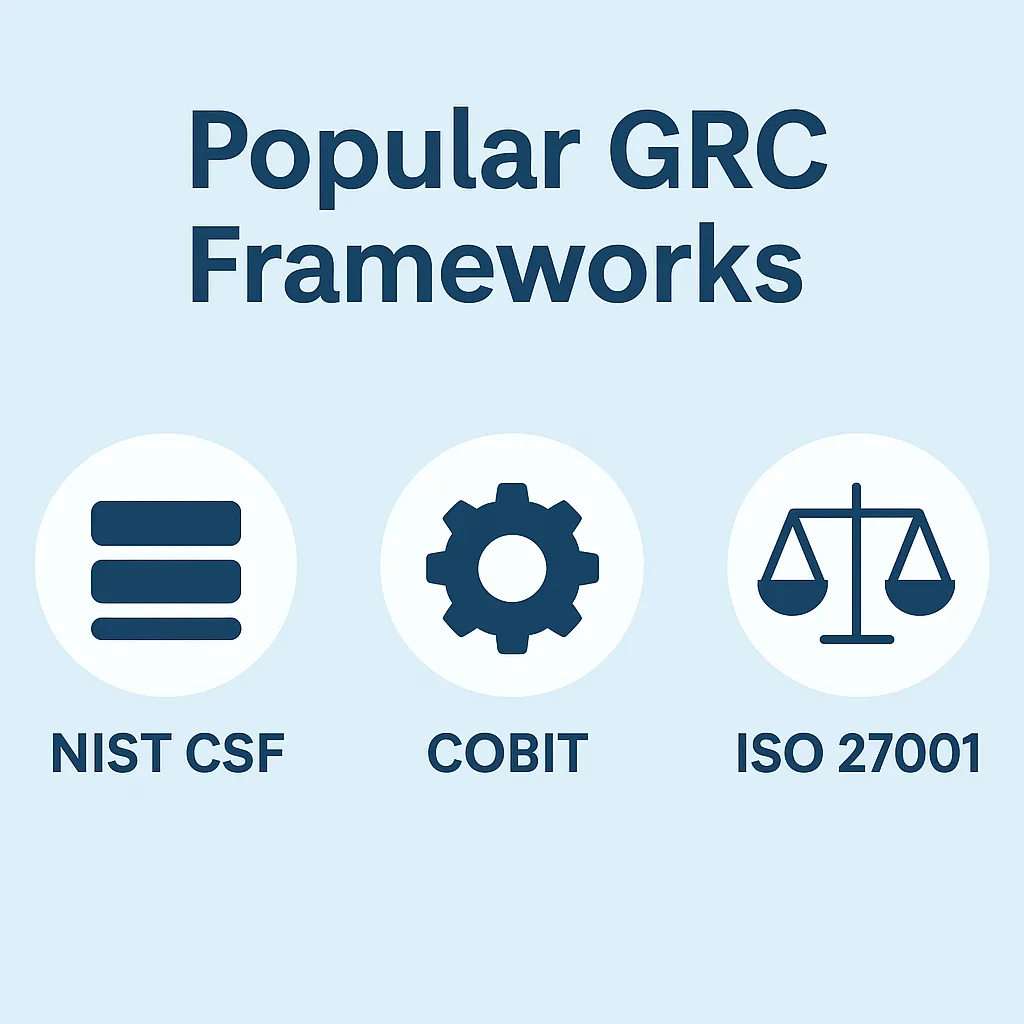
These frameworks define the rules, structure, and expectations for governance, risk, and compliance programs. Many organizations use a mix depending on industry and geography.
- NIST Cybersecurity Framework (CSF)
A flexible, tiered framework from the U.S. National Institute of Standards and Technology. Built around five core functions: Identify, Protect, Detect, Respond, and Recover. Ideal for aligning risk management with business objectives and scalable across industries. - ISO/IEC 27001
A globally recognized standard for Information Security Management Systems (ISMS). It provides a formal specification for risk-based security controls and is often used to achieve certification for demonstrating security maturity to partners and regulators. - COBIT (Control Objectives for Information and Related Technologies)
Created by ISACA, COBIT focuses on IT governance and control. It bridges the gap between technical controls and business goals, often used by organizations with mature IT processes and regulatory exposure. - COSO ERM
More finance and audit-focused, but relevant to cyber risk. The COSO Enterprise Risk Management framework is often used in heavily regulated industries for aligning operational risk with strategic objectives. - HIPAA Security Rule / PCI DSS / GDPR / DORA
These are regulatory-specific standards. While not full frameworks, they define precise security requirements and are often mapped to broader GRC systems for enforcement and auditing
Popular GRC Tools

These platforms operationalize GRC, connecting policies to systems, automating assessments, and enabling real-time risk visibility.
- ServiceNow GRC
Enterprise-grade, highly customizable. Integrates with ITSM, CMDB, vulnerability scanners, and cloud environments. Excellent for complex organizations needing tailored workflows and dashboarding. - RSA Archer
One of the most mature and comprehensive GRC platforms. Offers deep capabilities in risk management, compliance, third-party governance, and audit management. Ideal for regulated industries. - LogicGate
A flexible, no-code platform known for ease of use and quick deployment. Strong in risk management and compliance workflows. Often used by mid-sized organizations scaling their GRC maturity. - OneTrust GRC
Known for privacy and data governance, but expanding into broader GRC capabilities. Great for companies navigating GDPR, CCPA, and global privacy regulations. - Drata / Vanta / Secureframe
These are newer, cloud-native tools focused on automated compliance. Excellent for startups and SaaS companies pursuing SOC 2, ISO 27001, or HIPAA certification. Fast setup, real-time monitoring, and tight integration with cloud services. - RiskLens
Specializing in cyber risk quantification using the FAIR model. Helps organizations put a financial value on risk exposure, critical for budget planning and board-level reporting.
GRC vs. Traditional Security Programs
| Feature / Focus | Traditional Security Program | GRC in Cybersecurity |
| Primary Goal | Protect systems and data | Align security with business, risk, and law |
| Approach | Technical and reactive | Strategic and proactive |
| Risk Management | Informal, IT-driven | Formalized, cross-functional, quantifiable |
| Compliance | Audit-focused, manual | Continuous, automated, policy-driven |
| Reporting | Technical metrics (logs, alerts) | Business metrics (KRIs, KPIs, risk dashboards) |
| Stakeholder Involvement | Mostly IT and security teams | Involves legal, HR, risk, and executive teams |
| Tool Integration | Point solutions with limited interoperability | Unified platforms with automation and mapping |
| Scalability | Struggles with complexity | Designed for growth and regulatory evolution |
| Incident Response | Tactical containment | Structured response with post-incident review |
| Decision Support | Based on tech severity | Based on business impact and risk tolerance |
Traditional security programs focus heavily on technical defenses firewalls, antivirus, patching, and intrusion detection. While essential, these approaches are often reactive, siloed, and tactically driven.
GRC in cybersecurity, on the other hand, introduces a strategic, integrated model that aligns security with business operations, risk tolerance, and regulatory demands.
Here’s how they stack up across key dimensions:
1. Strategic Focus
- Traditional Security:
Primarily operational. Focuses on protecting infrastructure and responding to technical threats. - GRC:
Strategic and cross-functional. Ties security to business goals, legal risk, and enterprise-wide decision-making.
2. Risk Management
- Traditional Security:
Risk is often assessed ad hoc or as part of compliance audits. Prioritization tends to be based on severity rather than business impact. - GRC:
Implements continuous, structured risk assessments using quantifiable models. Prioritizes based on financial impact, regulatory exposure, and organizational tolerance.
3. Compliance Handling
- Traditional Security:
Treats compliance as a side task. Often, reactive approaches focus on passing audits rather than embedding controls. - GRC:
Integrates compliance into daily operations. Automates control monitoring and creates auditable, traceable systems across all business units.
4. Visibility and Reporting
- Traditional Security:
Metrics are typically technical (e.g., number of blocked attacks, patches applied). Limited executive visibility. - GRC:
Offers high-level dashboards, board-ready reporting, and KPIs that reflect business risk, compliance status, and strategic readiness.
5. Responsiveness and Adaptability
- Traditional Security:
Responds to incidents and adjusts based on known vulnerabilities or detected threats. - GRC:
Builds in feedback loops to adapt governance, update risk registers, and evolve controls based on incident outcomes and threat intelligence.
6. Integration with Business Functions
- Traditional Security:
Mostly operates within IT or InfoSec teams. Limited engagement with legal, HR, finance, or executive leadership. - GRC:
Bridges IT, legal, compliance, and executive roles. Encourages shared ownership of risk and decision-making across departments.
7. Scalability and Maturity
- Traditional Security:
Can be effective in smaller or less regulated environments. Scalability often becomes an issue as complexity grows. - GRC:
Designed to scale with organizational growth, regulatory demands, and evolving threat landscapes. Suitable for enterprise-grade security maturity.
Common Pitfalls and Misconceptions
1. Confusing Compliance with Security
What happens:
Organizations chase audit checkmarks SOC 2, ISO 27001, and HIPAA, thinking that passing an audit means their systems are secure. In reality, many high-profile breaches occurred in environments that were fully compliant on paper.
Why it’s a problem:
Compliance frameworks are often outdated, abstract, and not tailored to your actual threat model. Attackers don’t care if your controls align with policy; they care about exploitable gaps.
Fix it:
Use compliance as a baseline. Then layer on real-time threat intelligence, adversary simulations, and dynamic controls that evolve with your environment.
2. Overcomplicating with Framework Overload
What happens:
Companies try to implement every framework under the sun, NIST, ISO, COBIT, CIS, GDPR, CCPA, etc., resulting in overlapping controls, duplicated work, and audit fatigue.
Why it’s a problem:
More frameworks = more complexity = less clarity. Teams waste time reconciling control matrices instead of addressing actual risk.
Fix it:
Select two or three core frameworks that match your regulatory needs and risk appetite. Use crosswalks strategically, not blindly.
3. Buying Tools Without a Strategy
What happens:
Executives invest in top-tier GRC platforms expecting them to “solve” governance and compliance issues. But without processes, roles, and defined use cases, the tool becomes shelfware.
Why it’s a problem:
GRC is not a tech product, it’s a discipline. Tools are just force multipliers. Without proper planning, you’re automating dysfunction.
Fix it:
Build your GRC blueprint first: define risk models, governance structure, workflows, and metrics. Then choose tools that align with that vision.
4. Isolating GRC from Technical Operations
What happens:
GRC lives in a compliance bubble. Security engineers don’t engage, devs don’t read the policies, and IT thinks it’s someone else’s job.
Why it’s a problem:
Your policies don’t mean much if the people building and defending systems aren’t using or enforcing them. Silos kill GRC.
Fix it:
GRC should be operationally embedded. Integrate with SIEMs, SOARs, ticketing systems, and asset inventories. Make GRC data actionable, not just reportable.
5. Lack of Executive Engagement
What happens:
The board and C-suite treat GRC like IT plumbing. There’s no visibility, budget, or urgency until after a breach or fine.
Why it’s a problem:
Without leadership buy-in, GRC can’t drive cultural change, enforce tough decisions, or secure long-term investment.
Fix it:
Translate cyber risk into business language. Show how risk ties to financial loss, regulatory liability, and brand damage. Use real incidents and trend data, not fear-mongering.
Read More On: NotEvil Search Engine: How It Works and What You Can Find
6. Stale Risk Registers
What happens:
Risk registers are created once a year, filled with vague threats like “cyber attack” or “data breach”, and never revisited.
Why it’s a problem:
Static registers become irrelevant fast. New threats, technologies, and business changes make old risks obsolete or underweighted.
Fix it:
Make the risk register a living system. Update it quarterly (at least), feed it with threat intelligence, and tie risks to control effectiveness metrics.
7. Ignoring the Human Factor
What happens:
Organizations rely on annual training modules and policy acknowledgment clicks as their main human-layer defense.
Why it’s a problem:
Attackers exploit human behavior constantly. Real-world attacks rely on phishing, social engineering, and accidental exposure, not failed firewalls.
Fix it:
Run real simulations, track behavior over time, and build security champions inside departments. Reward good habits and respond to risky behavior with coaching, not blame.
The Future of GRC in Cybersecurity
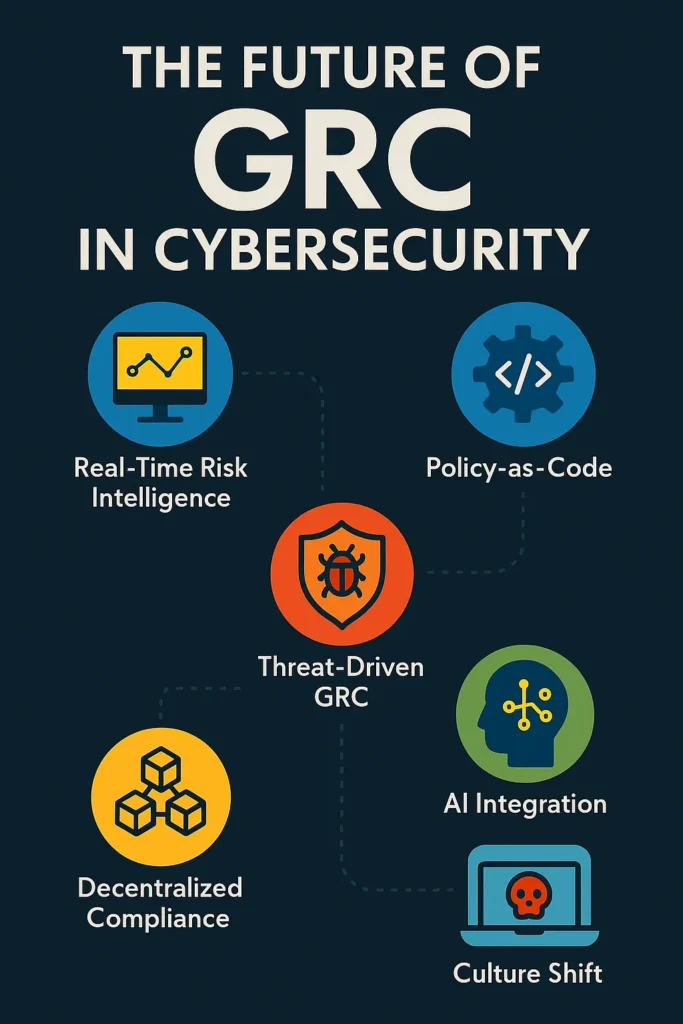
GRC used to be the graveyard of innovation. It was where creativity went to die under piles of regulatory paperwork and outdated risk matrices.
But the terrain has shifted permanently. In an age of AI-generated exploits, ransomware-as-a-service, and digital mercenaries-for-hire, the GRC status quo is not just obsolete, it’s dangerous.
Read More On: How Can Generative AI Be Used In Cybersecurity
Here’s how GRC is evolving from a bureaucratic relic to a real-time, code-integrated defense mechanism.
1. Real-Time Risk Intelligence, Not Quarterly Guesswork
Traditional GRC workflows rely on point-in-time assessments and audits that are outdated the moment they’re signed off. In 2025, that’s suicidal.
The future is about:
- Continuous control monitoring (CCM) powered by security telemetry.
- Live dashboards that reflect actual control effectiveness, not just policy intentions.
- Automated evidence collection, where systems document their compliance posture in real time.
This isn’t just better security, it’s operational survival.
Read More On: Cybersecurity YouTube Channels: Top 10 You Must Follow [2025]
2. Policy-as-Code: Where Governance Meets Git
Forget Word docs and stale SharePoint folders. Governance is moving to where the real action is: the codebase.
- Policy-as-code tools like Open Policy Agent (OPA), HashiCorp Sentinel, and Rego let orgs write security and compliance rules in declarative code.
- Version-controlled policies become testable, auditable, and deployable across infrastructure.
This means:
- Your security posture is now part of your CI/CD pipeline.
- Non-compliant code doesn’t ship. No exceptions.
- Governance is baked in, not bolted on.
3. Threat-Driven GRC > Compliance Theater
For too long, GRC has been about passing audits, not stopping threats. But as ransomware gangs become more sophisticated than most nation-states, organizations are waking up to a hard truth: Compliance is not security.
- Future GRC will align risk management with real-world threats, not checkbox frameworks.
- Expect more orgs to embrace cyber threat intelligence (CTI) to inform GRC decisions.
- Risk quantification will get sharper, using tools like FAIR (Factor Analysis of Information Risk) to speak the language of dollars and downtime.
4. AI is a Double-Edged GRC Weapon
AI is already rewriting the GRC playbook:
- AI can automate policy writing, compliance mapping, and risk scoring.
- LLMs can analyze massive troves of risk documentation, reducing human bottlenecks.
But here’s the twist: AI also creates new governance challenges.
- You now need to govern the AI itself, monitoring data provenance, bias, model drift, and hallucination risk.
- Expect to see the rise of AI governance frameworks as part of enterprise GRC stacks.
5. Decentralized Compliance and the End of Gatekeepers
What if you didn’t need to prove compliance to a regulator because the proof was built into the system?
- With blockchain-based attestations and smart contracts, compliance can become a state, not an exercise.
- Imagine a world where cloud providers, vendors, and internal teams sign tamper-proof attestations to demonstrate policy conformance.
It’s radical, but it’s coming, and it kills off the middleman-heavy, manual audit processes that dominate today.
6. Culture Shift: Hackers in the GRC Room
This might be the biggest disruption of all: GRC is becoming less about red tape and more about resilience and adaptability.
- Red teams and threat modelers are influencing enterprise risk appetite.
- CISOs are bringing hacker culture into risk conversations.
- Instead of aiming for “perfect compliance,” the goal is survivability under attack.
The boardroom is starting to speak the language of zero-trust, blast radius, and kill chains. That’s a revolution.
TL;DR: GRC Is Evolving or Dying
- GRC that can’t keep up with real-time threats is already irrelevant.
- If your GRC isn’t code-aware, automation-friendly, and threat-aligned, it’s a liability.
- The future of GRC is fast, autonomous, and hacker-informed.
The orgs that understand this will build adaptive defenses. The rest? They’ll be breached, audited, and left wondering what went wrong.
Read More On: 10 Online Best Dark Web Search Engines for Tor Browser
Final Thoughts
So, what is GRC in cybersecurity today? It’s no longer just a checkbox exercise designed to keep auditors happy.
It’s the framework that should help you survive the next breach, adapt to unknown threats, and prove your integrity without drowning in bureaucracy.
True GRC is evolving from static documents to dynamic systems, from manual reviews to automated enforcement, from compliance theater to threat intelligence.
And the organizations that embrace this shift will stop treating GRC as a regulatory burden and start using it as a competitive weapon.
Ignore the glossy vendor pitches and outdated standards. GRC isn’t about looking secure, it’s about being resilient. And in a world where attackers move faster than your quarterly audit, only the bold will stay standing.
Frequently Asked Questions
Why is traditional GRC broken?
Because it was designed for a world of spreadsheets and slow-moving threats. Today’s attacks are automated, polymorphic, and AI-enhanced. Traditional GRC is reactive, manual, and often divorced from actual threat intelligence. It creates the illusion of control without providing real resilience.
Is compliance the same as security?
Not even close. Compliance is about meeting minimum standards. Security is about surviving sophisticated adversaries. The smartest organizations treat compliance as a baseline, not a goal. True security means going beyond checklists and aligning with real-world threats.
How does AI impact the future of GRC?
AI is a game-changer on both sides. It can streamline compliance, analyze risk faster, and auto-generate audit reports. But it also introduces new governance risks like biased models, opaque decision-making, and attack surfaces that didn’t exist before. GRC now has to account for both defending with AI and defending against it.
Does GRC require coding?
Not necessarily. You can build a solid career in cybersecurity even in GRC without writing a single line of code. Roles like Information Security Analyst or GRC Analyst often focus more on risk frameworks, policy enforcement, and regulatory compliance than programming. That said, coding skills (especially for policy-as-code or automation) are becoming a big advantage in modern GRC environments.
Is GRC part of ERP?
Yes, GRC and ERP often intersect. Governance, Risk, and Compliance helps ensure that enterprise systems, including Enterprise Resource Planning (ERP) platforms, are secure, aligned with business goals, and compliant with regulations. Integrating GRC into ERP is crucial for securing business operations and ensuring audit-readiness across finance, HR, and supply chain systems.
Is an audit part of GRC?
Absolutely. Auditing is a core function within the GRC ecosystem. A GRC audit examines whether an organization’s security and compliance processes meet internal policies and external regulations. It’s how you find gaps, fix them, and prove you’re not just talking the talk, you’re walking it.






