Do you need a degree for cybersecurity? Not necessarily. While a degree can open doors, many cybersecurity professionals break into the industry through certifications, hands-on experience, and self-taught skills.
Employers increasingly value practical knowledge, critical thinking, and a strong grasp of security tools over formal education.
Cybersecurity is a booming field where cyber threats are escalating, and cybersecurity professionals are more in demand than ever.
This growing interest leads many to ask: Do you need a degree for cybersecurity? The short answer is no, not always.
While having a degree in computer science, information security, or a related field can certainly be helpful, it is no longer the only path into the industry.
Today’s employers often prioritize real-world skills, certifications like CompTIA Security+ or CEH, and hands-on experience over traditional academic credentials.
Whether you’re a career changer, a recent graduate, or someone passionate about cybersecurity, this guide will walk you through what matters most in building a successful cybersecurity career, with or without a degree.
Do You Need a Degree for Cybersecurity?

The question “Do you need a degree for cybersecurity?” is one of the most commonly asked by aspiring professionals entering the field, and the answer is more nuanced than a simple yes or no.
Modern cybersecurity strategies rely heavily on practical skills, problem-solving abilities, and a continuous learning mindset, not just academic qualifications.
While a degree in cybersecurity, computer science, or information technology can certainly help, it is not mandatory for breaking into the industry.
Many professionals have successfully launched their cybersecurity careers without a college degree, leveraging certifications, hands-on labs, internships, bug bounty programs, open-source contributions, and self-study to build a strong portfolio and skill set.
That said, having a degree can provide several advantages:
- It may fulfill job requirements in government or large enterprise roles.
- It helps build a theoretical understanding of cryptography, networks, and systems.
- It can improve long-term career growth and leadership opportunities.
However, the cybersecurity field values skills over titles.
Certifications such as CompTIA Security+, CEH (Certified Ethical Hacker), OSCP (Offensive Security Certified Professional), and CISSP (Certified Information Systems Security Professional) are highly respected and often more practical for proving your expertise than a degree alone.
Many companies today, especially those adopting modern cybersecurity strategies, prioritize real-world capabilities such as configuring secure networks, detecting threats, and implementing Zero Trust Network Access (ZTNA) models over formal credentials.
As a result, it’s increasingly common to see job postings that mention “degree preferred” rather than “degree required.”
In summary, a degree is helpful but not essential for a cybersecurity career. What matters most is your ability to demonstrate security skills, adapt to emerging threats, and stay updated with the latest tools and frameworks in cybersecurity.
Read More On: What Is GRC in Cybersecurity? Everything You Should Know
Pros and Cons of Having a Cybersecurity Degree

Pros
1. Structured Knowledge Foundation
A cybersecurity degree offers a comprehensive curriculum covering essential domains like network security, cryptography, secure software development, digital forensics, and ethical hacking.
It builds a structured understanding of attack vectors, defense strategies, and compliance frameworks (NIST, ISO 27001, CIS Controls) that are crucial for navigating the threat landscape.
2. Industry Recognition and Certifications
Many cybersecurity programs integrate or prepare students for key certifications such as CompTIA Security+, CISSP, CEH, and OSCP.
These credentials increase your credibility and marketability in a competitive job market.
3. Access to University Resources
Students gain access to research labs, cyber ranges, faculty expertise, and internship pipelines.
These environments provide hands-on experience with real-world attack simulations, red team/blue team operations, and incident response training, all essential for building tactical skills.
4. Network Building and Career Pathways
A degree often comes with connections: alumni networks, job placement services, and access to federal or defense sector opportunities that require formal education.
Some government cybersecurity roles (e.g., NSA, DoD) strongly prefer or mandate a degree.
5. Better Entry-Level Opportunities
In HR-filtered hiring systems, a cybersecurity degree can get your resume past the ATS (Applicant Tracking System) and onto a hiring manager’s desk.
It signals formal training in infosec fundamentals, making you a more palatable risk for entry-level hires.
Cons
1. High Cost, Low ROI for Some Roles
Many security practitioners, especially in offensive security, bug bounty, or pentesting, argue that degrees are overpriced and unnecessary. A self-taught hacker with a GitHub full of exploits or CTF wins can often outpace a grad with a generic B.S. in Cybersecurity.
Tuition debt can delay your ability to invest in certifications, home labs, or real-world experience.
2. The Curriculum Often Lags Behind Threat Reality
Universities can be slow to adapt. While cybercriminals iterate daily, academic programs may still teach outdated tools (e.g., focusing on Windows 7 exploits or deprecated protocols) or theoretical models instead of live-fire exercises.
The best attackers aren’t learning from textbooks, they’re in forums, reverse-engineering malware, and fuzzing code.
3. Doesn’t Guarantee Skill or Street Cred
In cybersecurity, competence is king. You can’t fake packet analysis or bypass endpoint detection with a diploma. Real-world scenarios demand adaptability, tool fluency (Wireshark, Burp Suite, Metasploit, etc.), and hacker intuition things no degree can guarantee.
4. Gatekeeping and Elitism
The degree requirement can act as a gatekeeper, disproportionately affecting brilliant autodidacts or those from nontraditional backgrounds.
Some companies overemphasize formal education, excluding talented individuals who’ve proven their skills in bug bounty platforms, open-source contributions, or underground communities.
5. Not Always Aligned with Hacker Culture
A degree is designed for the workforce, not the rebellion. If you’re drawn to cybersecurity because you love bending systems, exploring the edge cases, and thinking like a threat actor, academia may feel restrictive or sterile. The real hackers often come from the streets, not the lecture halls.
Alternatives to a Cybersecurity Degree
You don’t need a four-year degree to break into cybersecurity. That’s a myth perpetuated by outdated HR systems and institutions clinging to their tuition pipelines. The truth? There are leaner, more tactical ways to build a career in cybersecurity that skip the debt and hit the skills directly.
Here’s a breakdown of the best alternatives to a traditional cybersecurity degree:
1. Cybersecurity Certifications
Certs are the industry’s currency, especially for proving specific skill sets. Unlike degrees, they’re focused, faster, and employer-recognized.
Essential Entry-Level Certs:
- CompTIA Security+ – Great for beginners, covers core security concepts.
- CompTIA CySA+ / PenTest+ – Intermediate level, good for defenders (blue team) and attackers (red team).
- Cisco CCNA Security – Focuses on network security.
- GIAC Security Essentials (GSEC) – Broad but respected.
Advanced/Elite Certs:
- OSCP (Offensive Security Certified Professional) – A badge of honor for ethical hackers. Real-world hacking lab included.
- CISSP (Certified Information Systems Security Professional) – Management-focused, often required for senior roles.
- GCIH, GPEN, GXPN – SANS/GIAC certs that dive deep into incident handling, penetration testing, and exploit development.
Pro tip: Pair certs with hands-on labs like TryHackMe or Hack The Box to show you’re not just book-smart.
2. Cybersecurity Bootcamps
Bootcamps are immersive, skill-driven training programs, usually 12 to 24 weeks, that aim to make you job-ready, fast.
What to expect:
- Real-world scenarios, red vs blue team exercises.
- Resume and job interview prep.
- Cost ranges from $5,000 to $20,000, often with job guarantees or income-share agreements.
Top Picks:
- SANS CyberTalent Immersion Academy
- Flatiron School Cybersecurity Bootcamp
- Springboard Cybersecurity Career Track
- Evolve Security Academy
They won’t spoon-feed you theory. They’ll drop you into the trenches.
3. Self-Taught and Hacker Routes
You can teach yourself everything if you’ve got grit, curiosity, and an internet connection. This is how many of the world’s top hackers started. Not in classrooms, but in IRC channels, forums, and GitHub.
Tools and Platforms:
- Hack The Box, TryHackMe, OverTheWire – For hands-on hacking labs.
- CTFs (Capture The Flag) – Gamified hacking challenges. Sites like CTFtime.org track global competitions.
- YouTube, Blogs, Twitter – Follow real hackers and security researchers. Learn from their code, write-ups, and walkthroughs.
- Books – Start with The Web Application Hacker’s Handbook, Black Hat Python, and Practical Malware Analysis.
Bonus: Build a portfolio. Write up your exploits, publish your scripts, share your lab notes. Your GitHub and blog are your new resume.
4. Open Source Contributions and Bug Bounties
Contributing to security tools or hunting for bugs on platforms like HackerOne or Bugcrowd builds real-world cred. And you get paid for it.
Skills you demonstrate:
- Vulnerability discovery
- Reverse engineering
- Responsible disclosure
- Tool development
This is where theory meets the streets. And recruiters notice.
5. Community Colleges and Online Courses
Low-cost, flexible, and sometimes better aligned with industry needs than big-name universities.
Best platforms:
- Cybrary
- Coursera (Stanford, IBM, etc.)
- Udemy (look for top-rated infosec instructors)
- edX (HarvardX, MITx)
You can mix and match courses based on your interests, including red teaming, incident response, malware analysis, and more.
Top Cybersecurity Certifications That Employers Value

The cybersecurity industry is flooded with certifications. Some are respected. Some are resume filler. If you’re serious about building a real career in security, you need to know which ones employers care about.
1. CISSP (Certified Information Systems Security Professional)
Provider: (ISC)
Level: Advanced
Best for: Security architects, CISOs, and senior engineers
Why it matters
CISSP is widely seen as the benchmark for senior-level cybersecurity roles. It shows you understand how to build and manage security programs at scale. It is also compliant with government frameworks like DoD 8570.
What it covers
- Risk management and governance
- Security architecture and engineering
- Identity and access control
- Cryptography and secure communication
- Compliance and legal frameworks
Bottom line
CISSP is great if you’re aiming for leadership. It’s not about hands-on hacking. It’s about strategy and systems thinking.
2. OSCP (Offensive Security Certified Professional)
Provider: Offensive Security
Level: Advanced
Best for: Penetration testers, red teamers, and exploit developers
Why it matters
OSCP proves that you can actually hack into systems in a controlled, professional environment. The exam is a live penetration test. No multiple choice, just real attacks and real documentation.
What it covers
- Buffer overflows and custom exploit development
- Privilege escalation on Linux and Windows
- Post-exploitation and pivoting
- Manual enumeration and scripting
- Report writing and documentation
Bottom line
If you want to be taken seriously in offensive security, this is the cert to get. It shows you can think like an attacker and deliver results.
3. CompTIA Security+
Provider: CompTIA
Level: Entry-level
Best for: Newcomers, SOC analysts, and IT staff moving into security
Why it matters
Security+ is a baseline cert used across both public and private sectors. It is a required credential for many government and DoD roles.
What it covers
- Basic threat types and attack methods
- Network architecture and secure protocols
- Risk management and compliance basics
- Identity management and access control
- Incident response procedures
Bottom line
It will not make you an expert, but it will get you past HR filters. Pair it with hands-on practice to make it count.
4. CEH (Certified Ethical Hacker)
Provider: EC-Council
Level: Intermediate
Best for: Junior pentesters and analysts in government or compliance-heavy roles
Why it matters
CEH is widely recognized and helps tick boxes for employers who need to meet audit or contract requirements. It is also a common first step into offensive security.
What it covers
- Reconnaissance and scanning
- Exploitation tools and techniques
- System hacking and malware analysis
- Web application vulnerabilities
- Wireless, cloud, and social engineering attacks
Bottom line
CEH focuses on tools more than concepts. It is a good entry point, but if you want credibility in the hacker community, aim higher.
5. GSEC (GIAC Security Essentials Certification)
Provider: GIAC via SANS Institute
Level: Intermediate
Best for: Blue teamers, defenders, and network security professionals
Why it matters
GSEC is respected in industries like finance, healthcare, and critical infrastructure. It is one of the few certs that combines theory with deep technical coverage.
What it covers
- TCP/IP analysis and packet inspection
- Network and endpoint defense strategies
- Cryptographic standards and protocols
- Incident handling and threat detection
- Authentication and access management
Bottom line
If you are serious about defensive security and can get your employer to cover the cost, GSEC is worth every penny.
6. CISM (Certified Information Security Manager)
Provider: ISACA
Level: Managerial
Best for: CISOs, security managers, and GRC professionals
Why it matters
CISM is tailored for people leading cybersecurity programs. It connects business goals with security strategy. It is often required for executive-level roles in enterprise environments.
What it covers
- Security governance and frameworks
- Enterprise risk assessment and control
- Program development and resource management
- Incident response and legal compliance
Bottom line
CISM is not technical. It is strategic. If your job involves aligning security with business risk, this cert shows you know how to lead.
7. Google Cybersecurity Certificate and IBM Cybersecurity Analyst
Provider: Coursera (Google and IBM)
Level: Entry-level
Best for: Beginners, career changers, and students
Why it matters
These are newer certs but gaining respect as affordable gateways into the industry. They include hands-on labs and cover the basics in a digestible way.
What they cover
- Security fundamentals and core concepts
- Network defense and monitoring
- SIEM tools like Splunk and QRadar
- Threat intelligence and analysis
- Real-world simulations and case studies
Bottom line
These certs will not replace CISSP or OSCP, but they are solid launchpads for people without a traditional tech background.
Skills Needed for a Career in Cybersecurity

The cybersecurity industry thrives on skill, not just credentials. With attacks evolving faster than most schools can update their curriculum, the real question many ask is this: Do you need a degree for cybersecurity? The honest answer is no, not necessarily. What you need are skills that prove you can defend, attack, analyze, and adapt.
1. Master the Fundamentals
If you don’t understand how systems and networks work, you’re a liability. Start with the basics.
What to focus on:
- IP networking, subnets, routing, DNS, and firewalls
- Operating systems, especially Linux and Windows internals
- Command-line fluency
- Virtualization tools like VirtualBox or VMware
- Basic scripting in Bash, Python, or PowerShell
This is your foundation. Everything builds from here.
2. Understand Threats and Risks
Cybersecurity is not about locking everything down. It’s about managing risk intelligently.
Learn how to:
- Map attack surfaces using tools like threat modeling and ATT&CK
- Prioritize vulnerabilities based on real-world impact
- Communicate risk to technical and non-technical stakeholders
- Think like an attacker to protect like a defender
This is where you start thinking strategically, not just tactically.
3. Offensive Security Knowledge
To beat attackers, you need to understand their playbook.
Core skills:
- Scanning and enumeration
- Web app attacks like SQL injection and XSS
- Network attacks and privilege escalation
- Social engineering tactics
- Red team tactics and penetration testing methodology
Even defenders need some red team mindset.
4. Defensive Operations
This is the bulk of cybersecurity jobs. You need to know how to detect and respond fast.
Key areas:
- SIEM tools like Splunk or ELK
- Intrusion detection and response workflows
- Log correlation and incident triage
- Malware detection and sandboxing
- Endpoint and network hardening
Good defenders are obsessive about details and fast under pressure.
5. Cloud and DevSecOps Skills
Most infrastructure lives in the cloud. Your skills need to follow.
What to learn:
- AWS, Azure, or GCP security tools
- IAM configuration and access policies
- Kubernetes and container security
- CI/CD pipeline security checks
- Automation tools like Terraform and Ansible
Modern security means securing code as it ships.
6. Digital Forensics and Incident Response (DFIR)
When the breach happens, you need to know what went wrong and how to fix it.
Core competencies:
- Memory and disk analysis
- Network packet capture and timeline reconstruction
- Chain of custody and evidence handling
- Real-time response and communication
- Reporting that informs action, not just CYA
IR is the difference between recovering fast and making headlines.
7. Communication and Mindset
Technical skill alone isn’t enough. You need to communicate, think critically, and stay curious.
Build these habits:
- Write clean, concise reports
- Translate tech risk into business impact
- Ask why and dig deeper
- Collaborate across teams
- Learn fast and adapt faster
The best cybersecurity pros are thinkers, not just tool jockeys.
How to Get Your First Job in Cybersecurity Without a Degree

The cybersecurity industry is one of the few fields where skill still beats pedigree. Companies are desperate for people who can secure networks, catch threats, and think like attackers.
The question isn’t whether you need a degree, it’s whether you can deliver.
1. Learn the Fundamentals
You can’t protect what you don’t understand. Before anything else, you need to master the basics of computing and networking.
Key areas to study:
- Networking: IP, TCP/UDP, DNS, firewalls, routing
- Operating Systems: Linux command line, Windows internals
- Security Concepts: Confidentiality, Integrity, Availability (CIA triad), encryption, firewalls
- Basic Scripting: Python, Bash, PowerShell
Plenty of free or cheap resources exist. Use platforms like TryHackMe, Hack The Box, YouTube, and open courseware from MIT or Stanford.
2. Build a Lab and Get Hands-On
Certs and courses are great, but nothing beats doing the work. Set up a home lab to simulate attacks, defenses, and real-world scenarios.
Tools to use:
- VirtualBox or VMware
- Kali Linux for offensive tools
- Windows 10 for blue team simulations
- Wireshark, Nmap, Burp Suite, Metasploit
Document everything you do. Treat each project like portfolio material.
3. Earn the Right Certifications
You don’t need a degree, but you should still show proof of skills. Certs are the most efficient way to bypass gatekeepers.
Recommended starter certs:
- CompTIA Security+: For basic knowledge and HR filters
- Google Cybersecurity Certificate: Practical, affordable, entry-level
- eJPT or PNPT: Beginner-friendly hands-on pentesting
- OSCP (eventually): If you want to go full red team
Skip overpriced fluff. Focus on certs that demonstrate real skill or meet job requirements.
4. Build a Cyber Resume Without Experience
No job? No problem. Focus on what you’ve done, not what you’ve been paid for.
What to include:
- Homelab projects with links to GitHub repos or writeups
- CTFs and Hack The Box completions
- Certifications and coursework
- Blogs, tutorials, or videos you’ve made
- Community contributions or open-source work
Be honest, but show passion. Prove you’re already doing the work.
5. Start with the Right Roles
You won’t be a pentester on day one. Get your foot in the door with entry-level security or IT positions.
Entry roles to target:
- SOC Analyst (Tier 1)
- IT Support with a security focus
- Junior Security Analyst
- Vulnerability Management Assistant
- Threat Intel Researcher (entry level)
These roles teach you the stack, expose you to tooling, and give you real-world muscle.
6. Network Like Hell
You don’t need a degree, but you do need a reputation. Build it by getting involved.
Places to connect:
- Twitter (InfoSec Twitter is real and active)
- LinkedIn (post what you’re working on, share insights)
- Local DEF CON groups, BSides, and meetups
- Discord and Reddit communities (NetSec, Cybersecurity, etc.)
Talk less about getting a job, more about what you’re building and learning. The offers will come.
7. Apply Strategically
Don’t shotgun your resume. Apply where it makes sense, and tailor your approach.
Tips:
- Look for companies hiring based on skills, not just degrees
- Apply to MSPs and startups, they care more about results
- Use a project or write-up as your “cover letter.”
- Show up prepared to talk about real problems you’ve solved
Focus on jobs that value practical ability over paper credentials.
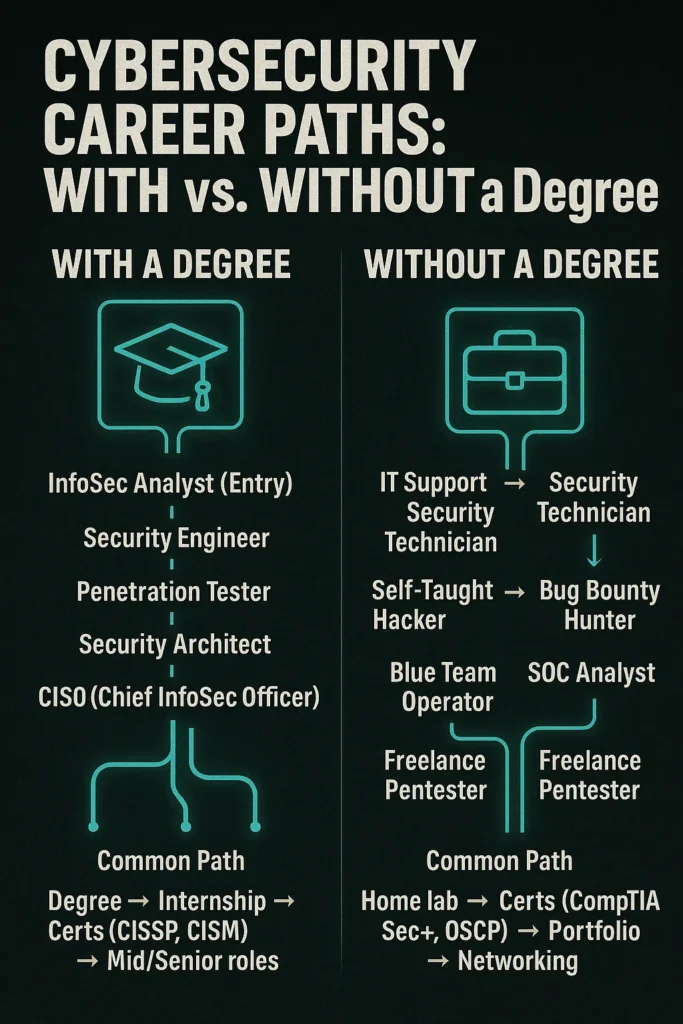
Cybersecurity Career Paths With and Without a Degree
Cybersecurity doesn’t care where you went to school. It cares if you can stop an intrusion, detect a breach, or write a script that keeps attackers out.
The idea that you need a degree to work in cybersecurity is outdated. Sure, it can help with certain jobs or get past HR filters. But it’s not a requirement, not even close.
This guide breaks down the most common career paths in cybersecurity, showing how you can enter and grow in the field with or without a degree. Whether you’re coming from a computer science program or learning from scratch at your kitchen table, there’s a path for you.
Career Paths With a Degree
A cybersecurity, computer science, or information systems degree can be a fast track into the industry, especially in large enterprises, government jobs, or compliance-heavy sectors. These paths often offer structure, benefits, and upward mobility.
1. Security Operations Center (SOC) Analyst
What you do: Monitor alerts, investigate threats, and escalate incidents.
Why it fits: Degree programs often prepare students for Tier 1 SOC roles.
2. Security Engineer
What you do: Build and manage firewalls, VPNs, IDS/IPS, and endpoint defenses.
Why it fits: A CS degree helps with infrastructure and systems-level knowledge.
3. Risk and Compliance Analyst
What you do: Audit systems, ensure regulatory compliance, and map risk to controls.
Why it fits: Business-facing roles value formal education and documentation skills.
4. Cybersecurity Consultant
What you do: Advise clients on security posture, perform assessments, and write reports.
Why it fits: Many firms expect degrees for consulting roles.
5. Security Architect
What you do: Design secure infrastructure for cloud, on-prem, or hybrid environments.
Why it fits: Senior-level roles are often reached after years of experience and academic grounding.
Career Paths Without a Degree
If you’re self-taught, bootcamp-trained, or coming from a non-traditional background, your entry point may look different, but the long-term potential is the same. The key is to prove your skills early and show you can deliver results.
1. SOC Analyst (Entry Level)
How to get in: Learn log analysis, detection tools, and incident response basics.
Certs to target: CompTIA Security+, Google Cybersecurity Certificate
Why it works: SOC jobs often focus on practical skills over academic pedigree.
2. Junior Penetration Tester
How to get in: Build a home lab, learn exploitation techniques, and pass a hands-on cert.
Certs to target: eJPT, PNPT, OSCP
Why it works: Offensive security values proof-of-work over credentials.
3. Bug Bounty Researcher
How to get in: Start hunting on platforms like HackerOne or Bugcrowd.
Why it works: You’re judged solely on what you find and report not your resume.
4. Malware Analyst or Reverse Engineer
How to get in: Learn x86/ARM assembly, use tools like Ghidra, IDA, and x64dbg.
Why it works: This is a niche area where passion and curiosity often outperform degrees.
5. Cloud Security or DevSecOps Engineer
How to get in: Learn AWS, Docker, CI/CD pipelines, and IaC tools.
Certs to target: AWS Security Specialty, Terraform, Kubernetes security
Why it works: Cloud skills are in demand and highly practical.
Skills That Matter More Than a Degree
Regardless of how you enter the field, there are core competencies every cybersecurity pro needs.
- Networking and system administration
- Scripting and automation (Python, Bash, PowerShell)
- Incident response and log analysis
- Penetration testing and vulnerability management
- Threat intelligence and forensics
- Cloud architecture and identity management
These are skills you can learn on your own. The internet is your university and your lab.
How to Choose Your Path
Ask yourself:
- Do I want to defend systems or break them?
- Do I prefer hands-on work or strategic planning?
- Am I more technical or more analytical?
- Do I want to work in corporate, freelance, or government environments?
Then reverse-engineer the path to get there. Identify the job title, study the required skills, and start building a portfolio that proves you can do it.
Final Thoughts
Do you need a degree for cybersecurity? The answer is no. What you need are skills, proof that you can solve problems, and the mindset to keep learning.
A degree might help in some corporate or government roles, but it’s not a requirement to build a serious career in this field.
The cybersecurity world values action over theory. If you can secure systems, find vulnerabilities, analyze threats, or respond to incidents with clarity and speed, you will get hired. The path may be different without a degree, but the destination is the same.
Focus on building, breaking, learning, and showing your work. The opportunities are out there with or without a diploma.
Frequently Asked Questions
Is a college degree required to start a career in cybersecurity?
No, a college degree is not mandatory to begin a career in cybersecurity. Many professionals enter the field through self-study, certifications, and hands-on experience. Employers often prioritize practical skills and demonstrable knowledge over formal education.
What alternative pathways exist for entering cybersecurity without a degree?
Individuals can pursue certifications such as CompTIA Security+, Certified Ethical Hacker (CEH), or GIAC Security Essentials (GSEC). Engaging in online courses, participating in cybersecurity bootcamps, and gaining practical experience through labs or internships are effective ways to build a foundation in cybersecurity.
Are there specific cybersecurity roles accessible without a degree?
Yes, roles like Security Analyst, Penetration Tester, and Security Consultant are attainable without a degree, provided you have the necessary skills and certifications. Employers value hands-on experience and the ability to demonstrate proficiency in relevant tools and methodologies.
Can someone with no experience start a career in cybersecurity?
Yes. You can enter the cybersecurity field without prior experience by learning on your own, earning industry-recognized certifications, and applying for beginner-level roles that offer hands-on exposure.
Is it too late to start a career in cybersecurity at 30?
Not at all. Starting cybersecurity at 30 or older is completely viable. The industry values practical skills, life experience, and commitment over age. Many professionals enter the field later in life and build successful, long-term careers.






