As cybersecurity becomes increasingly complex, many professionals and aspiring infosec specialists are asking: Does cybersecurity require coding?
The short answer isn’t always black and white; it depends on the role, the domain, and the depth of expertise required.
Does Cybersecurity Require Coding?
Yes, cybersecurity does require coding in many technical domains.
While some roles, like governance or Tier 1 SOC analysis, may not need deep programming knowledge, areas such as penetration testing, threat hunting, reverse engineering, and DevSecOps rely heavily on scripting and software development skills.
Understanding how to write code not only gives security professionals the ability to automate tasks and analyze malicious scripts but also enables them to write custom detection logic, develop exploits, and secure software pipelines.
In this guide, we’ll break down which cybersecurity paths require coding, which ones don’t, and why programming is becoming an essential skill set for staying ahead of modern threats.
Cybersecurity by Domain: Where Coding Really Matters

1. Penetration Testing & Red Teaming
Coding Level: High
Pen testers and red teamers simulate real-world attacks. To stay stealthy and effective, they rely heavily on custom scripts and tooling.
Coding use cases:
- Writing custom exploits in Python or C
- Automating payload generation and delivery (e.g., with Metasploit modules)
- Developing shellcode or modifying existing proof-of-concept (PoC) scripts
- Obfuscating code to evade EDR/XDR solutions
- Building C2 (Command and Control) frameworks in Go or .NET
Key languages: Python, Bash, PowerShell, Go, Assembly, C
Read More On: What Is Baiting in Cyber Security? Don’t Fall For It
2. Threat Hunting & Detection Engineering
Coding Level: Moderate to High
Blue teamers who proactively hunt threats and write detections benefit significantly from scripting skills.
Coding use cases:
- Writing YARA rules and Sigma signatures for malware and anomaly detection
- Parsing and correlating large volumes of logs with Python or Regex
- Automating IOC enrichment with APIs (VirusTotal, MISP, Shodan)
- Scripting threat hunting queries in tools like Splunk, ELK, or Sentinel
Key languages/tools: Python, Regex, KQL (for Azure), Bash, REST APIs
Read More On: How to Start a Cyber Security Company Off-Grid
3. Security Automation & SOAR Engineering
Coding Level: Moderate to High
SOAR (Security Orchestration, Automation, and Response) engineers reduce manual workload in a SOC by integrating systems via code.
Coding use cases:
- Writing Python playbooks to automate incident response workflows
- Building connectors to integrate SIEMs, ticketing systems, and threat intel feeds
- Developing scripts for auto-remediation (e.g., isolate endpoints or block IPs)
Key languages/tools: Python, JavaScript, PowerShell, REST APIs, JSON, YAML
Read More On: Cyber Security vs Software Engineering: Code or Defend?
4. Malware Analysis & Reverse Engineering
Coding Level: High
Analysts in this field dissect malicious code and binaries to understand attacker behavior.
Coding use cases:
- Debugging malware samples using tools like Ghidra, IDA Pro, or x64dbg
- Writing decryption tools or unpackers in C/C++
- Analyzing system calls, DLL injections, and API hooks
- Automating static or dynamic analysis processes
Key languages: C, C++, Assembly, Python, Rust
5. DevSecOps & Security Engineering
Coding Level: High
Security engineers embed security in DevOps pipelines, requiring fluency in programming and scripting.
Coding use cases:
- Writing IaC (Infrastructure as Code) scripts in Terraform, Ansible, or AWS CloudFormation
- Automating container security scanning and vulnerability detection in CI/CD
- Developing custom security tooling for build pipelines
- Reviewing application code for security flaws
Key languages/tools: Python, JavaScript, Go, YAML, Shell scripting, Jenkins, GitHub Actions
6. Digital Forensics & Incident Response (DFIR)
Coding Level: Moderate
Forensics specialists and responders often need to automate evidence collection and initial analysis.
Coding use cases:
- Scripting triage tools for endpoint data collection
- Automating forensic artifact parsing (e.g., event logs, registry hives, memory dumps)
- Writing post-incident scripts to document and archive findings
Key languages: Python, PowerShell, Bash
7. GRC, Audit, and Policy Roles
Coding Level: Low to None
While not technical in the programming sense, some light scripting can still enhance productivity.
Coding use cases:
- Writing compliance checks for systems (e.g., CIS Benchmarks via scripts)
- Automating spreadsheet processing or reporting with Python
- Using scripting in tools like Nessus or OpenSCAP for audit automation
Key languages (optional): Python, VBA, shell scripting
Read More On: What Is GRC in Cybersecurity? Everything You Should Know
Cybersecurity Roles That Don’t Require Coding
| Role | Requires Coding? | Key Skills |
|---|---|---|
| SOC Analyst (Tier 1) | No | SIEM, Alert Triage, Incident Handling |
| GRC Analyst | No | Frameworks, Documentation, Policy Writing |
| Security Awareness Specialist | No | Training, Communication, Phishing Simulation |
| Compliance/Privacy Officer | No | Legal, Regulatory Knowledge, Risk Handling |
| Third-Party Risk Analyst | No | Vendor Audits, Questionnaires, Excel |
You don’t need to be a programmer to start a career in cybersecurity. Many vital roles focus on analysis, compliance, and communication rather than writing code.
1. Security Analyst (Tier 1 SOC)
What They Do: Monitor alerts, triage incidents, and escalate real threats.
Skills Required: Understanding of security tools (like SIEMs), threat intelligence, and good communication.
Coding? Not required, most work involves interpreting logs and using pre-configured dashboards.
Ideal for beginners starting in cybersecurity without a technical background.
2. GRC Analyst (Governance, Risk & Compliance)
What They Do: Ensure the organization adheres to frameworks like ISO 27001, NIST, and HIPAA.
Skills Required: Policy writing, risk assessments, and audit processes.
Coding? Not needed a strong understanding of documentation and standards is more valuable.
Perfect for those with legal, auditing, or policy-making backgrounds.
3. Security Awareness & Training Specialist
What They Do: Design and deliver cybersecurity training to employees, run phishing simulations, and promote a culture of security.
Skills Required: Communication, empathy, and some familiarity with threat behavior.
Coding? No, this is about influencing human behavior, not machines.
Great for educators, HR professionals, and communicators.
4. Compliance or Privacy Officer
What They Do: Handle data protection, legal compliance (e.g., GDPR), and work closely with legal and IT teams.
Skills Required: Privacy law, regulatory compliance, and data classification.
Coding? No, it’s more legal than technical.
Strong analytical and legal reasoning will go further than coding here.
5. Third-Party Risk Analyst
What They Do: Assess the security posture of vendors and partners through questionnaires and audits.
Skills Required: Risk frameworks (like FAIR), Excel, and reporting.
Coding? Not necessary, evaluation and documentation are key.
If you’re analytical and process-driven, this role is for you.
Benefits of Coding in Cybersecurity Even If It’s Not Required
Even if the answer to does cybersecurity requires coding is often “not always,” having coding skills gives you a real edge.
From boosting efficiency to improving threat analysis, here’s how coding enhances your cybersecurity capabilities.
1. Automation of Repetitive Tasks
Manual analysis doesn’t scale. Coding allows you to:
- Automate log parsing and IOC extraction
- Schedule tasks like asset scanning, patch checks, or user behavior tracking
- Write custom scripts to triage alerts and generate reports in real time
Example: A Python script can automatically pull threat intel from APIs like VirusTotal, enrich alert data, and create a ticket in your SOAR platform.
Sample Python Script: IOC Enrichment Using VirusTotal API
import requests
API_KEY = “your_virustotal_api_key”
IP = “8.8.8.8”
url = f”https://www.virustotal.com/api/v3/ip_addresses/{IP}”
headers = {
“x-apikey”: API_KEY
}
response = requests.get(url, headers=headers)
if response.status_code == 200:
data = response.json()
malicious = data[‘data’][‘attributes’][‘last_analysis_stats’][‘malicious’]
print(f”[+] IP: {IP} – Malicious Detections: {malicious}”)
else:
print(f”[-] Error fetching data for IP {IP}: {response.status_code}”)
Use Case:
You can integrate this into your alert triage flow, enriching indicators directly in your SOC workflow.
2. Customized Tooling and Scripting
Off-the-shelf tools aren’t always flexible. Coding lets you:
- Modify open-source security tools (e.g., modify a Metasploit module)
- Build quick and dirty scripts tailored to your environment
- Develop internal tools for niche use cases like specific cloud configurations or log sources
3. Enhanced Threat Analysis and Detection
Understanding how code behaves allows you to:
- Analyze obfuscated malware scripts and exploit payloads
- Write more accurate detection rules for SIEM platforms
- Reverse engineer suspicious binaries with greater confidence
Example: Being able to decode a base64-encoded PowerShell payload during an incident can drastically speed up the response.
4. Stronger Offensive and Defensive Skills
Knowing how attackers build and modify their code helps you:
- Identify patterns in attacks (code reuse, logic flaws, etc.)
- Replicate techniques in lab environments for testing controls
- Harden defenses with more precision, especially in EDR or firewall configurations
5. Career Growth and Versatility
Employers value infosec professionals who can write code because:
- You’re more adaptable across red, blue, and purple teams
- You can transition into engineering, research, or architecture roles
- You contribute to cross-functional projects involving dev, cloud, and ops teams
Fact: Most senior cybersecurity roles, from Security Architects to Threat Researchers, list coding or scripting experience as a preferred or required skill.
Most Valuable Programming Languages by Use Case

Choosing the right programming language often depends on the job you want done. From powering websites and mobile apps to detecting cyber threats and training machine learning models, different languages excel in different areas.
If you’ve ever wondered does cybersecurity requires coding, the answer lies in the role some security paths demand scripting and automation, while others rely more on conceptual expertise.
Web Development
Web development is broadly split into frontend, backend, and full-stack development. Here’s where each language shines:
- JavaScript Powers nearly every modern website. Works for both frontend and backend (via Node.js).
- TypeScript: A strongly typed superset of JavaScript. Great for large-scale frontend apps.
- HTML/CSS: While not programming languages per se, they form the structural and visual foundation of every website.
- Python: Backend development with Django or Flask is clean and scalable.
- PHP: Still dominant in CMS development, especially WordPress.
- Ruby: Known for fast prototyping with Ruby on Rails.
Cybersecurity & Automation
Security professionals often write scripts or tools to detect, automate, or simulate cyber activity. These are the go-to languages:
- Python: Unmatched versatility in automation, tool development, and scripting.
- Bash: Essential for Unix/Linux scripting.
- PowerShell: A must for scripting and automation in Windows environments.
- C / Assembly: Vital for writing exploits, shellcode, and reverse engineering.
- YARA / Sigma / Regex: Used to write detection rules and identify malicious patterns.
Data Science & Machine Learning
Data-driven applications need languages that make working with data easy and scalable:
- Python: Leads the ML world with libraries like NumPy, pandas, TensorFlow, and PyTorch.
- R: Excellent for statistical computing and visualizations.
- Scala: Used with Apache Spark for big data processing.
- Java: Popular in enterprise-grade big data systems.
- JavaScript (D3.js): For creating dynamic, interactive data visualizations in the browser.
Systems Programming
Systems programming requires speed, memory control, and low-level access:
- C: Powers operating systems, embedded devices, and firmware.
- C++: Offers object-oriented features with low-level control. Used in game engines and real-time systems.
- Rust: Modern, memory-safe alternative to C++. Gaining ground in performance-critical systems.
- Assembly: Required for reverse engineering, malware development, and firmware optimization.
Cloud, DevOps & Infrastructure
Infrastructure-as-code and automation rely heavily on scripting and declarative languages:
- Go (Golang): Ideal for building scalable cloud-native tools (e.g., Docker, Kubernetes).
- Python: Widely used for automation and cloud SDK integration.
- Bash: Still critical in DevOps pipelines.
- YAML: Used in Kubernetes configurations and GitHub Actions.
- HCL: Language used in Terraform for defining infrastructure.
AI, NLP & Deep Learning
If you’re diving into artificial intelligence and natural language processing, these languages matter:
- Python: Powers almost all mainstream AI frameworks (PyTorch, Keras, TensorFlow).
- Julia: Ideal for scientific computing with near-C-level performance.
- C++ / CUDA: For writing high-performance ML training or inference engines.
Mobile App Development
Mobile apps need platform-native or cross-platform languages:
- Kotlin: Google’s preferred language for Android apps.
- Java: Traditional Android development.
- Swift: Apple’s language of choice for iOS apps.
- Dart (Flutter): Cross-platform solution by Google.
- JavaScript (React Native): Web-to-mobile development using React Native.
Enterprise & Backend Systems
Large-scale systems in finance, healthcare, and enterprise rely on these stable, mature languages:
- Java: Backbone of enterprise systems, especially with Spring.
- C#: Dominates enterprise Windows applications.
- Python: Used for microservices, scripting, and backend APIs.
- Go: Growing fast in microservice architecture.
- Scala: Used in big data and financial backend systems.
Real-World Scenarios: Coding in Action

Let’s put these languages into context with real-world examples where they’re actively used to solve problems or build products:
- Python for Threat Detection: A security analyst uses Python to automate the parsing of log files from a SIEM tool like Wazuh or Sentinel, using Regex to extract Indicators of Compromise (IoCs) and trigger alerts for suspicious activity.
- Go in Cloud Infrastructure: DevOps engineers write Kubernetes controllers and plugins in Go to manage containerized apps at scale. Terraform, written in HCL, is used alongside Go-based tools to automate multi-cloud infrastructure.
- C++ in Game Development: Game developers at companies like Ubisoft or Epic Games use C++ to build the rendering engines that power high-performance games like Assassin’s Creed or Fortnite.
- JavaScript + React Native for Mobile: A startup builds a mobile app using JavaScript and React Native to deploy it on both Android and iOS, reducing time-to-market by avoiding separate native builds.
- Swift for iOS Health Apps: A healthcare tech company builds HIPAA-compliant iOS apps in Swift that sync securely with wearable devices and Apple HealthKit.
- R for Epidemiology: Data scientists in public health organizations use R to analyze disease spread patterns and visualize predictions with ggplot2.
- Rust in Browser Engines: Mozilla developed parts of its Firefox browser using Rust to enhance memory safety and performance, reducing common vulnerabilities like buffer overflows.
- Kotlin for Banking Apps: Android apps for banks like ING and Revolut are built using Kotlin to ensure modern code practices and better null safety.
These examples show that programming languages aren’t just theoretical tools; they directly drive real-world impact across industries like finance, cybersecurity, healthcare, gaming, and AI.
And if you’re still wondering, does cybersecurity require coding? Real-world roles like threat detection, log parsing, and rule automation clearly show that coding is a powerful asset, even if not mandatory for every role.
Learning Path: Going from Script Kiddie to Security Engineer
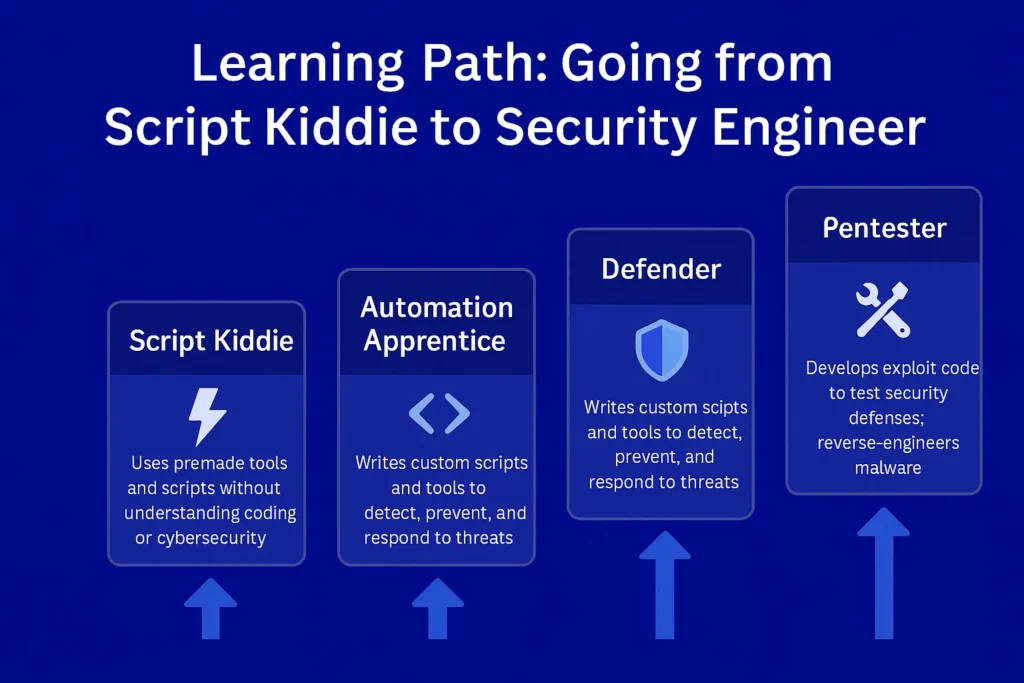
Starting as a beginner in cybersecurity can feel overwhelming, but a structured learning path can guide your journey from tinkering to a full-fledged engineering role:
- Script Kiddie Phase
- Tools: Metasploit, Nmap, Wireshark (used without a deep understanding)
- Focus: Learning the basics of networks, ports, and simple exploits
- Language: Start with Python and Bash for scripting
- Beginner Security Analyst
- Skills: Incident response, log analysis, basic alert triaging
- Tools: Splunk, Wazuh, SIEM dashboards, VirusTotal, Shodan
- Language: Master Python for automation and parsing logs
- Intermediate Security Engineer
- Skills: Writing detection rules (YARA, Sigma), scripting automations, threat hunting
- Tools: Elastic Stack, Suricata, Zeek, SOAR platforms
- Language: Expand to PowerShell, Regex, YAML
- Advanced Engineer / Red Team / Blue Team Specialist
- Skills: Exploit development, malware reverse engineering, detection engineering
- Tools: IDA Pro, Ghidra, Cuckoo Sandbox, custom-built tools
- Language: Learn C, C++, Assembly, and explore Rust for secure tooling
- Security Architect or Threat Intelligence Expert
- Skills: Designing secure infrastructure, integrating threat feeds, risk–based strategy
- Tools: Threat intel platforms, SIEM orchestration, attack simulation tools
- Language: Programming becomes less about code, more about understanding architecture and tool integration
With each level, your reliance on automation and custom coding increases, which answers the question, Does cybersecurity require coding?
Not always, but mastering the right language at the right time becomes essential for career growth.
Final Thoughts
Does Cybersecurity Require Coding?
The short answer? Not always, but it helps.
You don’t need to be a hardcore programmer to start in cybersecurity. Many entry-level roles focus more on analysis, monitoring, or policy work than actual coding.
However, as you move up the ladder, whether toward red teaming, threat hunting, or engineering, coding becomes a force multiplier.
Knowing how to script in Python, automate tasks in Bash or PowerShell, or write detection rules with YARA or Sigma can turn a good analyst into a great one.
It helps you automate, scale, customize, and understand what’s happening under the hood.
Think of coding not as a gatekeeper but as an enabler. The more technical you become, the more doors open and the more value you can bring to your team.
So if you’re serious about growth in cybersecurity, start learning to code. One script at a time.
Frequently Asked Questions
Is Cybersecurity Easier Than Coding?
Cybersecurity generally requires less coding than traditional software development. However, it demands a solid understanding of networks, operating systems, system administration, and core security concepts. While coding helps, deep technical awareness and critical thinking are more central to cybersecurity success.
Can a Non-Technical Person Learn Cybersecurity?
Absolutely. While cybersecurity is a technical domain, any motivated individual can become technical by learning the basics. Foundational knowledge in networking, system security, and threat awareness can be developed over time. Moreover, soft skills like communication, critical thinking, and project management are equally valuable, especially in roles like governance, risk, and compliance (GRC) or cybersecurity project coordination.
Will Cybersecurity Jobs Be Replaced by AI?
No, AI is not replacing cybersecurity professionals, but rather enhancing their capabilities. AI assists with threat detection, automation, and pattern analysis, but it can’t replicate human skills like strategic thinking, ethical judgment, or incident response decision-making. The future lies in human-AI collaboration, where professionals use AI tools to boost efficiency and accuracy.
What’s the Best Entry-Level Cybersecurity Certification?
CompTIA Security+ is one of the top certifications for beginners. It’s widely recognized, DoD 8570 compliant, and provides essential skills in system security, threats, risk management, and more. It’s a great starting point for those aiming to enter the field without prior experience.
What’s the Hardest Cybersecurity Certification?
The GIAC Information Security Fundamentals (GISF) is known to be among the most challenging. It covers a broad range of topics and demands a high degree of professional knowledge. The exam requires thorough preparation and tests both conceptual understanding and practical security skills.