Understanding the Dark Web
The dark web remains hidden from conventional search engines like Google and Bing, requiring specialized software such as the Tor Browser for access.
Unlike the surface web, the dark web operates through onion routing, ensuring anonymity and security. However, navigating it is challenging since many .onion sites frequently change domains or remain unindexed.
To simplify exploration, the best dark web search engines for Tor Browser help users find relevant content by indexing hidden websites and providing search capabilities similar to traditional search engines.
For individuals wishing to broaden their cybersecurity expertise, this list of the best cybersecurity YouTube channels offers professional views and updates on digital security trends.
In this article, we’ll highlight 10 top dark web search engines that make browsing the dark web more accessible.
Disclaimer: Always exercise caution, as the dark web contains potential risks such as scams, illegal content, and malware. Prioritize privacy and security while browsing.
How Tor Nodes Work to Keep You Anonymous
The Tor network relies on a series of relays, known as nodes, to anonymize your online activity. When you use the Tor Browser, your connection is routed through multiple Tor nodes, which include:
- Entry Node: The first relay that connects your device to the Tor network. It knows your real IP address but not your final destination.
- Middle Relay: The second relay in the chain, which simply forwards encrypted traffic to another node without knowing its origin or destination.
- Exit Node: The final relay in the chain, which decrypts your request and sends it to the target website. The exit node does not know who you are, but it can see the content you are accessing.
Importance of Exit Nodes
- The exit node is the last point before traffic reaches the open internet.
- Because exit nodes decrypt the last layer of encryption, they can see the unencrypted data if the website does not use HTTPS.
- Some malicious exit nodes may try to intercept sensitive information, so using HTTPS is crucial when browsing the dark web.
To explore the hidden web safely, the Best Dark Web Search Engines for the Tor Browser provide a way to find onion sites without exposing your identity.
These search engines specialize in indexing hidden services, making it easier for users to access content within the Tor network securely.
Each node knows only about the previous and next steps, making it nearly impossible to trace the original user’s IP address.
If you’re concerned about potential threats while browsing, try using our free Cybersecurity Risk Calculator to assess your risk level and take proactive steps to stay protected.
10 Best Dark Web Search Engines
1. Ahmia
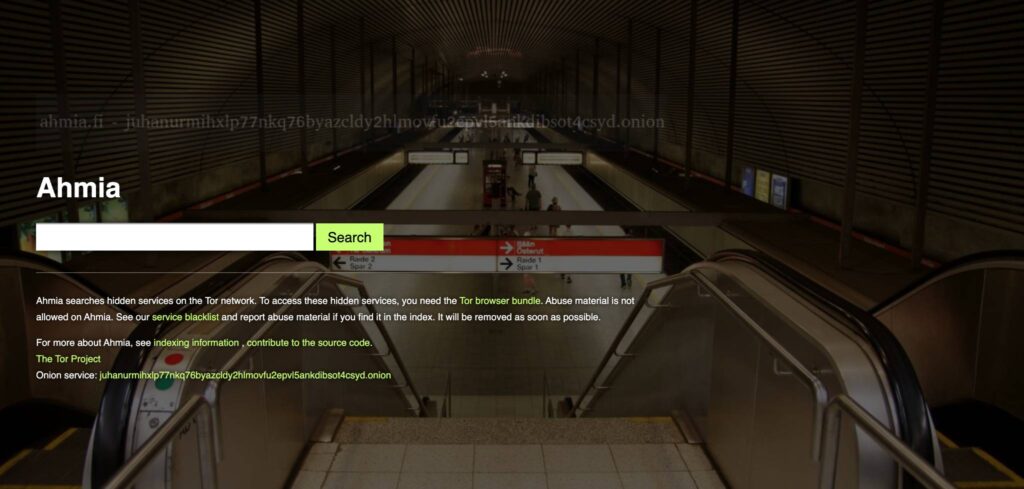
Overview:
- Ahmia focuses on indexing .onion sites exclusively from the dark web, rather than combining surface and dark web content.
- It is specifically built to enhance accessibility to hidden services within the Tor network. With a clean and user-friendly interface, Ahmia simplifies the process of discovering hidden services.
- As an open-source platform, it encourages transparency and community contributions. Additionally, it prioritizes user privacy and anonymity by operating entirely within the Tor network.
Key Features:
- Ahmia is accessible through the clear web and the Tor network, offering users flexibility in connecting.
- Its user-friendly design features a straightforward search bar, making it easy to locate hidden services.
- Search results are displayed with titles and descriptions to help users find relevant content efficiently.
- Ahmia employs content filtering to reduce exposure to illegal or harmful material on the dark web.
- Advanced search tools allow users to refine results by category, keyword, or indexing date for more precise searches.
- To protect user privacy, Ahmia does not store any identifiable search data or link queries to IP addresses.
- Security features such as HTTPS Everywhere integration add extra layers of protection while browsing.
- Regular transparency reports provide insights into indexed sites, filtering measures, and ongoing development efforts.
Why Use It?
- Simplified Access: Ahmia streamlines the search for hidden services by indexing Tor-based sites, eliminating the need for manual browsing or outdated link lists.
- Strong Privacy Measures: Ahmia upholds Tor’s core values by enabling anonymous access to deep web content without exposing user identities or locations.
- Content Moderation: To enhance user safety, Ahmia employs filtering mechanisms that help minimize exposure to illegal or harmful content while searching.
- Open-Source Transparency: With publicly available code, Ahmia fosters trust by allowing developers and researchers to inspect, modify, and improve its functionality.
- Community Collaboration: Ahmia benefits from ongoing contributions by security experts and developers, ensuring it remains an effective and secure search tool.
- Research and Analysis Tool: By indexing hidden services, Ahmia provides valuable insights into deep web trends, dark web marketplaces, and digital anonymity.
Read More On: What Is GRC in Cybersecurity? Everything You Should Know
2. Torch
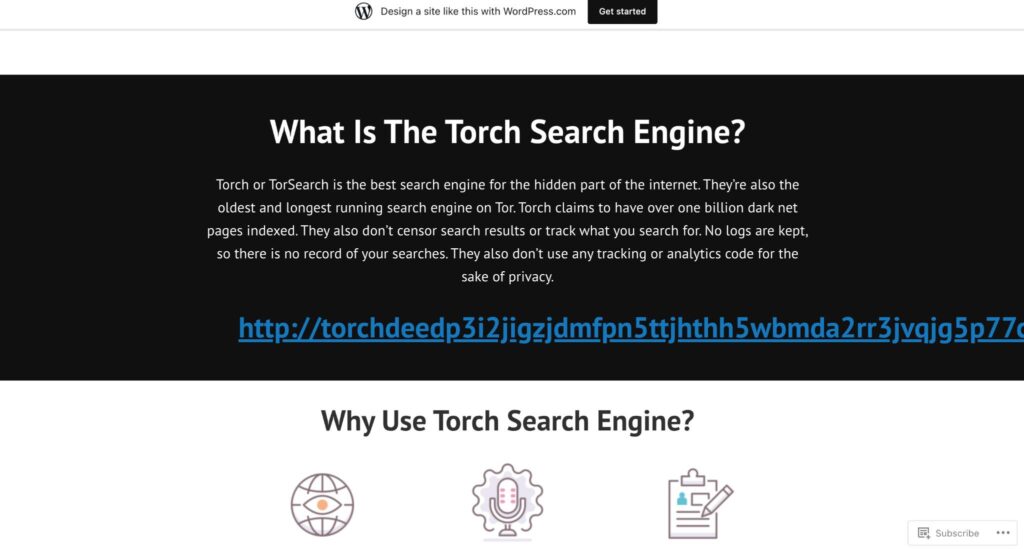
Overview:
- Torch is a leading dark web search engine with a vast index of .onion sites.
- It prioritizes user privacy by not storing search history or collecting user data.
- It ensures greater anonymity by preventing any tracking of user activity.
- It delivers uncensored search results, allowing unrestricted access to hidden content.
- It removes ads from search results, reducing the risk of exposure to malicious links or suspicious sites.
Key Features:
- Torch maintains a vast database of .onion websites, helping users find specific Dark Web content efficiently.
- It offers a simple and intuitive interface, allowing users to conduct searches with ease.
- It ensures user anonymity by preventing tracking of search activity and accessed websites.
- It delivers unfiltered search results without restrictions, providing full access to available content.
- It remains free to use, allowing anyone with a Tor browser to explore the Dark Web without limitations.
Why Use It?
- Torch protects user privacy by keeping searches and browsing activities untraceable, preventing surveillance.
- Researchers, journalists, and cybersecurity experts use Torch to find exclusive resources like leaked documents and niche forums.
- It provides unrestricted search results, enabling users to access information freely without censorship.
- By granting access to the Dark Web, Torch aids privacy-focused projects, including secure communication platforms and decentralized networks.
3. Not Evil
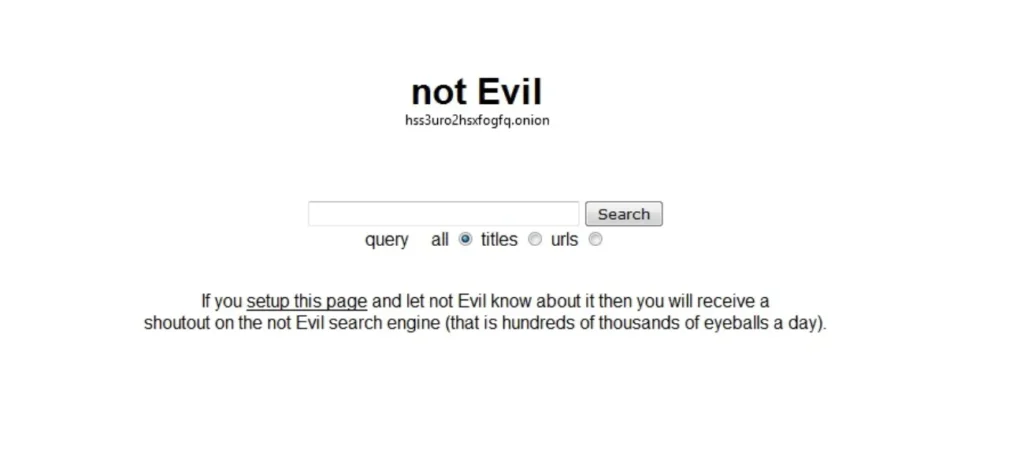
Overview:
- NotEvil brands itself as a “moral” dark web search engine.
- It crawls and indexes websites on the Tor network, allowing users to search them with a familiar interface.
- It filters out illegal and harmful content, such as drug and weapon marketplaces and sites that incite violence or hate.
- It applies ambiguous criteria for harmful content, which raises concerns about bias and censorship.
Key Features:
- NotEvil claims it filters out websites involved in illegal activities such as drug trafficking, weapons sales, or stolen data marketplaces.
- Criminals constantly innovate, so NotEvil might miss new or disguised illegal operations.
- NotEvil may provide a platform for accessing whistleblower content with anonymity, benefiting journalists and researchers.
- NotEvil offers a filtered search engine that can help users bypass government censorship in restricted countries.
- NotEvil delivers a familiar, user-friendly interface that simplifies navigation of the dark web for those unfamiliar with Tor.
- NotEvil enables keyword-based searches to help users easily locate relevant websites within the vast dark web.
Read More On: What Is Baiting in Cyber Security? Don’t Fall For It
Why Use It?
- NotEvil filters search results to protect users from overtly illegal or harmful dark web content, though caution remains necessary.
- Investigative journalists use NotEvil to access whistleblowing platforms and connect with sources in censored regions, even if relying solely on it might limit access to unfiltered data.
- Activists leverage NotEvil to retrieve censored information and engage with like-minded communities, despite potential gaps in its index.
- General users benefit from NotEvil’s familiar, user-friendly interface that simplifies finding privacy-focused content on the dark web.
- NotEvil enhances privacy by routing searches through Tor and anonymized links, although it does not guarantee complete anonymity against sophisticated tracking.
Curious how generative AI is being used to improve cybersecurity around tools like these?
Read the full breakdown here on how advanced AI models are shaping modern cyber defense.
4. Candle
Overview:
- The Candle search engine offers a unique way to explore the dark web.
- It provides access to anonymous .onion sites that regular search engines like Google cannot index.
- Users must use specialized software like Tor to navigate the dark web.
- Candle efficiently scans and retrieves hidden information from the dark web, making it accessible to users.
Key Features:
- Users can browse the web anonymously, protecting their identity and privacy in an era of frequent data breaches.
- The dark web grants access to unrestricted and uncensored information, unlike traditional search engines.
- Pairing browsing with services like Forest VPN enhances security, keeping online activity private and protected.
Why Use It?
- Candle offers a lightweight, user-friendly dark web search experience without ads, ensuring a distraction-free environment.
- It prioritizes user privacy by avoiding activity tracking or data storage, enhancing online anonymity.
- Candle helps users explore the dark web securely without leaving a digital footprint.
Read More On: Cyber Security vs Software Engineering: Code or Defend?
5. Phobos

Overview:
- Phobos features a minimalist user interface with only a search bar, making it easy to navigate.
- It stands out as the fastest search engine among those covered in this post.
- The creators of Phobos remain anonymous, as the site lacks an About Us or Contact Us page.
- The search engine’s creator previously promoted it on Reddit.
- When asked about plans, the creator stated they would keep the site running because it is “cheap to maintain and interesting to improve.”
Key Features:
- The system fully encrypts files under 1.5MB and partially encrypts larger files to enhance encryption speed.
- It encrypts smaller blocks of data within large files and stores a list of these blocks along with the key in the metadata at the file’s end.
- It scans for network shares within the local network.
- It maintains persistence by adding entries to the Startup folder and Run Registry key.
- It generates a target list of file extensions and folders for encryption.
- A watchdog process monitors and terminates applications that keep target files open to ensure successful encryption.
- It disables system recovery, backups, shadow copies, and the Windows firewall.
- It includes an embedded configuration with over 70 customizable options, encrypted using AES with a hardcoded key.
Why Use It?
- It features a simple search bar, making navigation easy and distraction-free.
- Compared to other dark web search engines, Phobos delivers results quickly.
- Like other dark web search engines, it does not track user activity or store search queries.
- Phobos indexes various .onion sites, allowing users to access a broader range of content.
- The creator keeps the site running because it is cheap to maintain and interesting to improve.
Read More On: How to Start a Cyber Security Company Off-Grid
6. DarkSearch
Overview:
- DarkSearch indexed and searched .onion sites on the dark web.
- It functioned as the “Google of the Dark Web,” offering users an easy way to find information across hidden services.
- Users could access information effortlessly without manually exploring the dark web.
Key Features:
- It indexed several .onion domains, allowing users to search the hidden web more effectively.
- Unlike other dark web search engines, DarkSearch has a simple interface.
- Initially, no Tor is required. It was formerly available over the clearnet, which meant that users did not require Tor to utilize it.
- It prioritized security and privacy by not logging user activity or tracking searches.
Why Use It?
- DarkSearch is no longer operational. It was taken down, and users looking for alternatives can use:
- Ahmia.fi (searches .onion links but is accessible on the clearnet)
- Haystak (a dark web search engine with a large database)
- DuckDuckGo’s .onion version (for private searches on the Tor network)
7. Haystak
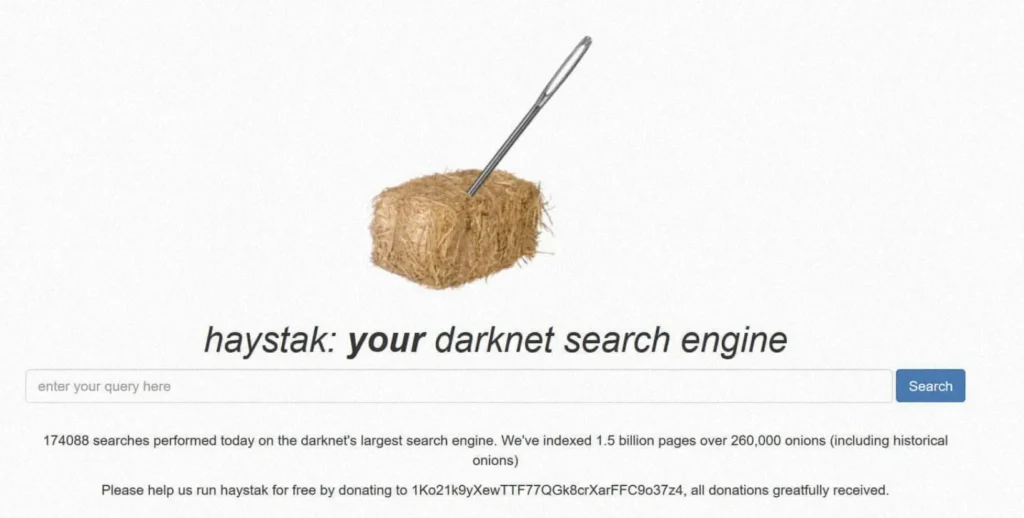
Overview:
- Haystack indexes over 1.5 billion dark web pages, making it one of the most comprehensive dark web search engines.
- It follows a freemium model, requiring payment to remove ads and access older website versions.
- Like DuckDuckGo, Haystack prioritizes user privacy and avoids tracking or monetizing personal data.
- It indexes various types of content, including websites, forums, and marketplaces, enabling anonymous searches.
- Many indexed sites may not function since most dark web sites disappear over time, leaving only a small percentage active.
Key Features:
- Haystak allows users to explore the dark web with ease.
- Its simple and clean interface simplifies navigation, even for those who aren’t tech-savvy.
- It has indexed over 1.2 billion pages across more than 260,000 websites.
- Users have rated it highly, with a 4.6 out of 5 stars on G2, reflecting its strong reputation.
- Haystak ensures privacy by not collecting or storing users’ personal information.
Why Use It?
- Haystak stands out as a unique search engine that provides a different experience from traditional ones.
- It helps users explore the dark web and is specifically built for the Tor network.
- Many consider it a top-rated dark web search engine due to its functionality and design.
- On G2, users rated Haystak highly, giving it an impressive 4.6 out of 5 stars.
- A 4.6-star rating reflects its strong reputation among feature-rich dark web search engines.
8. TorLinks
Overview:
- Tor Links serves as a backup directory for .onion sites when other directories become unavailable.
- It provides an alternative resource in case primary Tor directories, like the Hidden Wiki, go offline.
- Popular Tor sites face constant shutdown risks, making backups essential for accessibility.
- Users can rely on Tor Links to find dark websites even if other directories stop functioning.
Key Features:
- Backup Directory for .onion Sites, as it ensures access to dark web links if primary directories go offline.
- Alternative to Hidden Wiki as it provides a secondary resource for discovering dark web sites.
- Offers a collection of updated and working .onion links.
- Categorizes links into different sections like financial services, forums, and social networks.
- Helps users find important sites when other directories are down.
- Works best when accessed via the Best Dark Web Search Engines for Tor Browser to maintain anonymity.
Why Use It?
- Ensures access to dark web links when sites like the Hidden Wiki go offline.
- Organizes and provides verified .onion sites for secure browsing.
- Works with the Best Dark Web Search Engines for Tor Browser as it enhances privacy and ensures safe access to hidden services.
9. The Hidden Wiki
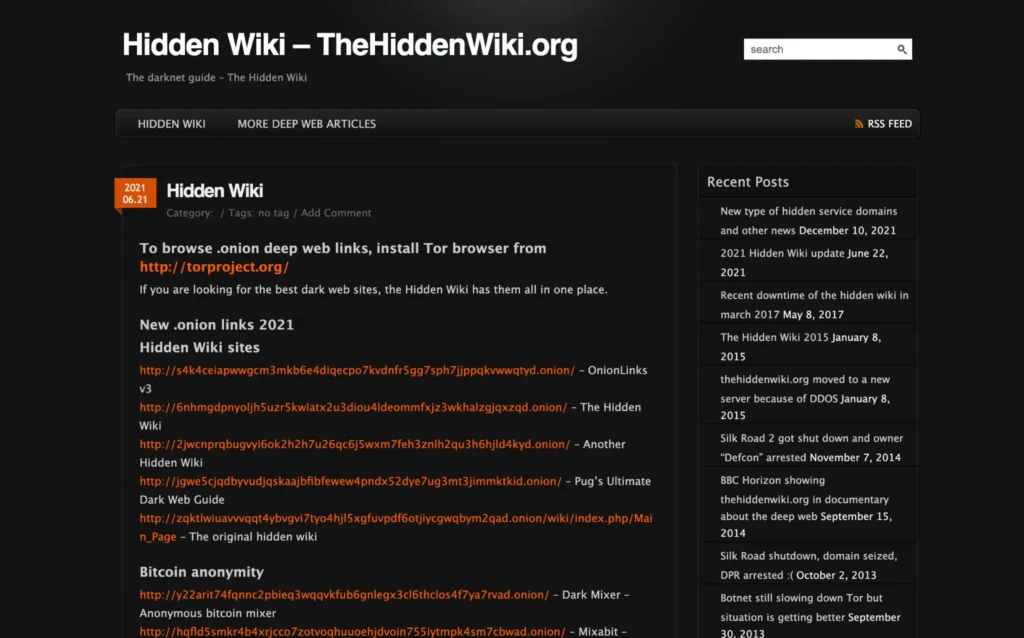
Overview:
- The Hidden Wiki operated as a dark web MediaWiki site and functioned as a Tor hidden service.
- Registered users could anonymously edit the wiki after signing up.
- The main page provided a directory of links to various .onion websites.
- Multiple .onion sites now host successor versions of the Hidden Wiki based on its mirrors.
- No single official version of the Hidden Wiki exists anymore.
- Some versions were created to maintain accessibility due to frequent downtime and instability.
- Others were launched to filter out links to child pornography.
Key Features:
- Lists various .onion websites, making it easier to navigate the dark web.
- Allows registered users to contribute and edit content while maintaining privacy.
- Operates as a Tor hidden service, ensuring user anonymity.
- Exists on various .onion domains to prevent data loss and ensure accessibility.
- Organizes dark web resources into sections like forums, marketplaces, and privacy tools.
- Relies on the community to update and verify links.
Why Use It?
- Serves as a starting point for exploring the dark web.
- Provides links to forums, privacy tools, and dark web markets.
- Uses Tor to ensure user identity protection.
- Helps users find verified and legitimate .onion links.
- Acts as a structured index for dark websites that search engines do not index.
10. Onion City
Overview:
- Onion.City offers a Google-like search engine for exploring the dark web without requiring Tor.
- Virgil Griffith, a programmer, developed Onion.City to provide a new way to search the dark web.
- The search engine indexes dark web content similarly to Google, retrieving results from its database based on user queries.
- Onion.City operates using the Tor2web proxy, enabling regular Internet users to access .onion domains.
- The proxy allows the search engine to explore .onion domains while remaining on the Tor anonymizer network.
Key Features:
- Provides a familiar search engine experience for .onion sites.
- Allows users to browse dark web content without using the Tor browser.
- Uses the Tor2web proxy to access .onion domains via regular web browsers.
- Crawls and indexes dark web content similar to how Google indexes the surface web.
- Enables users to search and access .onion sites without complex configurations.
- Operates within the Tor network to retrieve results while maintaining privacy.
- Searches a vast range of dark web content for various user queries.
Why Use It?
- Onion.City simplifies deep web searches by allowing users to explore darknet content from a regular, unsecured web browser.
- The search engine enables easy access to darknet content for the general public.
- It makes the darknet accessible to all users through standard browsing methods.
Final Thoughts
Navigating the dark web can be intriguing, but users must prioritize safety. The Best Dark Web Search Engines for the Tor Browser streamline access to .onion sites, offering an efficient way to explore hidden content.
To stay secure, always browse with the Tor Browser, enable HTTPS for data protection, and refrain from sharing personal information on unverified sites.
Caution is necessary, as some dark web content may be risky or illegal. However, the dark web also supports privacy-focused communities, whistleblower platforms, and other legitimate services.
Responsible browsing ensures a secure and ethical experience.
Have you used any of these dark web search engines? Let us know your experiences in the comments below!
Related Articles:
Top 10 Cybersecurity Forensic Tools For Ethical Hackers In 2025
Top 10 SIEM Use Cases for 5G Security
NotEvil Search Engine: How It Works and What You Can Find
Which Of The Following Is Not A Function Of A Cybersecurity Framework?
Frequently Asked Questions
Which search engine works best with Tor?
DuckDuckGo is the default search engine in the Tor Browser and is widely regarded as privacy-friendly. If you have specific concerns, sharing them could help us provide tailored recommendations.
Is there a better alternative to Tor?
A commonly used alternative to Tor is a Virtual Private Network (VPN), which ensures a secure and private internet connection. Unlike Tor, which anonymizes traffic by routing it through multiple relays, a VPN encrypts internet activity and directs it through a remote server.
Can Google index the dark web?
Google and traditional browsers like Chrome or Safari cannot be used to search the dark web. Instead, specialized software such as Tor or I2P is required to access dark web content.
Is the Tor Browser Safe?
Although the Tor Browser is often associated with the dark web, its use does not imply engagement in illegal activities. It is a valuable tool for many internet users seeking anonymity. Due to its operational design, Tor is generally considered safe, offering enhanced privacy and security through its onion routing technology.
What is Freenet on the Dark Web?
Freenet is a decentralized, encrypted, and open-source platform that allows users to communicate, share files, and access online content anonymously. It is designed to ensure privacy and censorship resistance, making it a part of the dark web.