What is baiting in cyber security? It’s a digital hustle where curiosity gets weaponized. Hackers bait the hook, you take it, and they’re in.
It’s a con as old as hacking itself, only now, it’s gone digital. Baiting exploits human instincts: curiosity, greed, and urgency.
A “lost” USB drive. A free movie download. A fake job offer. All lures are designed to get you to bite.
Once you do, the payload drops malware, installs it, and leaks credentials, making your system vulnerable to their control.
Baiting isn’t just phishing with flash; it’s a psychological exploit masked as convenience. Here’s how it works, why it still fools people, and how to avoid getting played.
What Is Baiting in Cyber Security?
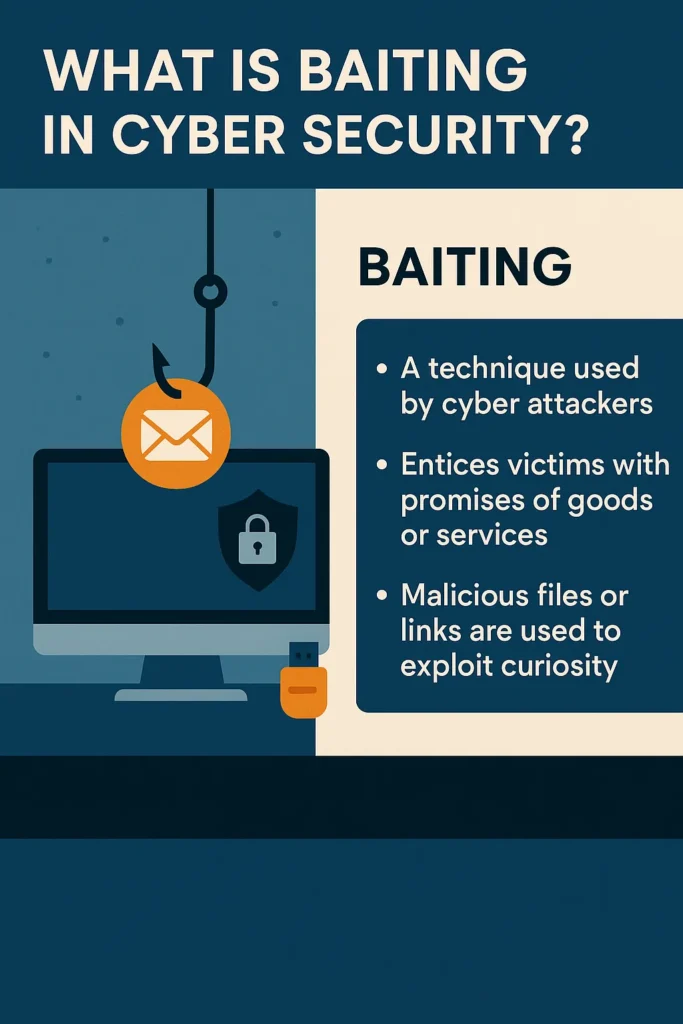
Baiting in cyber security is a digital trap designed to exploit one thing: human behavior. Think of it as a hacker’s version of fishing with dynamite, low effort, high return.
Instead of breaching firewalls or cracking encryption, the attacker counts on you to invite them in.
All it takes is one “harmless” action: plugging in a USB, clicking a download, scanning a QR code.
So, what is baiting in cyber security exactly? It’s a form of social engineering where attackers leave behind or offer something enticing, often physical, like a flash drive or virtual, like free media, pirated software, or fake cloud storage links.
The moment someone interacts with the bait, malware is executed, backdoors open, and control is ceded. It’s not a brute-force attack, it’s a human exploit.
What sets baiting apart from other cyber tricks?
- Phishing plays the role of the liar spoofed emails, fake logins, and impersonation.
- Pretexting plays the actor, building trust with fake scenarios, roles, and narratives.
- Baiting is the hustler; it just dangles something shiny and lets the victim do the rest.
The genius of baiting lies in its simplicity. It’s low-tech, high-impact, and disturbingly scalable. Attackers don’t need custom malware or nation-state budgets.
Just a believable lure and a willing target. In many cases, baiting is deployed in the wild through:
- Dropped USB drives near corporate buildings
- Torrented “cracked” versions of expensive software
- Fake browser updates on shady websites
- QR codes placed in public spots can lead to malicious payloads
Baiting works because humans are predictable. We trust what’s free. We click what’s easy. And in an age where convenience trumps caution, baiting thrives.
Read More On: Cyber Security vs Software Engineering: Code or Defend?
What is baiting in cyber security, then? It’s the art of hacking human instincts no zero-days required.
The Anatomy of a Baiting Attack
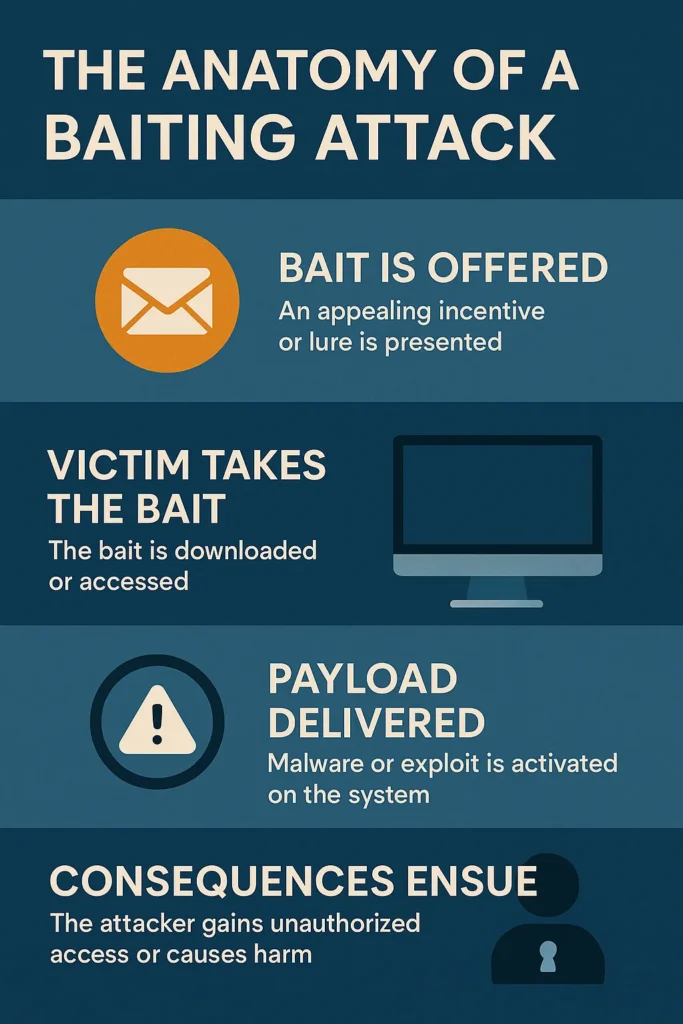
A baiting attack is a structured cyber threat that relies on social engineering and malware deployment to compromise systems. Unlike purely technical exploits, baiting weaponizes human curiosity to bypass digital defenses.
Here’s a step-by-step breakdown of how it works from setup to system compromise.
1. Recon and Targeting
Before deploying the bait, attackers often perform basic reconnaissance to identify high-value environments. This may include:
- Physical recon (offices, parking lots, events)
- Digital recon (forums, Discord groups, job platforms)
- Behavioral profiling (what kind of lure will the target bite?)
Baiting isn’t always random; advanced attackers tailor the lure to their target environment, especially in spear-baiting scenarios.
Read More On: What Is GRC in Cybersecurity? Everything You Should Know
2. Crafting the Payload
The attacker prepares a malicious payload, which may be:
- An infected USB drive (formatted with AutoRun malware, HID scripts, or preloaded payloads via Rubber Ducky devices)
- A trojanized application (e.g., a cracked Adobe installer with a bundled infostealer)
- A malicious QR code (leading to a fake update or credential harvester)
- A shortcut file (.LNK) disguised as a document, triggering PowerShell commands
The payload often leverages obfuscation (like Base64 encoding, macros, or staged execution) to evade antivirus and EDR systems.
Read More On: Does Cybersecurity Require Coding?
3. Lure Deployment
Attackers distribute the bait either physically or digitally:
- Dropping infected USBs near office buildings or in high-traffic areas
- Posting “free software” or “exclusive job files” in communities like Reddit, Telegram, or cracked software sites
- Embedding QR codes on fake posters, Wi-Fi login pages, or phishing emails
Each bait contains a high-impulse trigger curiosity (“What’s on this USB?”), urgency (“Job application deadline”), or reward (“Free premium tool”).
4. Execution Upon Interaction
When the target interacts:
- USB: On insertion, the device may auto-execute scripts or prompt a fake document to be opened, triggering PowerShell or cmd.exe.
- File download: User opens what seems like a PDF or EXE; malware executes silently in the background.
- QR code: Leads to a malicious URL that auto-installs spyware or prompts credential input via spoofed interfaces.
Attackers often use living-off-the-land (LotL) tactics, abusing built-in Windows tools (like WMI, regsvr32, or certutil) to avoid detection.
Read More On: Do You Need a Degree for Cybersecurity in 2025?
5. Persistence and Exploitation
Once inside, malware establishes persistence via:
- Registry keys (HKCU\Software\Microsoft\Windows\CurrentVersion\Run)
- Scheduled tasks
- DLL injection into trusted processes
Then it begins exploitation:
- Keylogging, screen capture, clipboard theft
- Credential scraping (from browsers, system memory, LSASS)
- Lateral movement using tools like PsExec or RDP
- Exfiltration via DNS tunneling, HTTP POST, or Telegram bots
Advanced payloads may include command-and-control (C2) frameworks like Cobalt Strike, Mythic, or custom Python implants.
6. Cleanup or Dormancy
Depending on objectives:
- Smash-and-grab attackers may encrypt files and drop ransom notes.
- Silent operators may leave backdoors or beacon silently, waiting for further instructions.
Either way, the attacker has bypassed digital perimeter defenses by using the most vulnerable vector: the human element.
TL;DR: A baiting attack is a hybrid exploit, part psychological, part technical. It blends social engineering with malware tactics, using tools from basic USB scripts to full C2 infrastructure.
What makes it dangerous is how little the user has to do; just one click or plug is enough.
Baiting in the Wild: Real Case Studies

Baiting attacks aren’t just theoretical they’ve been used in state-sponsored cyber warfare, corporate espionage, and everyday cybercrime. Below are some of the most compelling real-world examples that reveal just how dangerous and effective this tactic can be.
Case 1: Stuxnet – USB Bait Goes Nuclear
In one of the most famous cyberattacks in history, the Stuxnet worm was used to sabotage Iran’s nuclear program. But it didn’t spread through networks it entered via USB.
- How it happened: Intelligence agencies allegedly dropped infected USBs near Natanz nuclear facility employees. Someone picked one up, plugged it into an air-gapped system, and unknowingly triggered a worm that targeted Siemens PLCs running uranium centrifuges.
- Technical vector: Stuxnet exploited four zero-day vulnerabilities and used stolen digital certificates to appear legitimate.
- Impact: Over 1,000 centrifuges were destroyed without a single bullet fired.
- Lesson: Even top-tier physical security is useless if human curiosity isn’t locked down.
Case 2: Google’s USB Experiment (2016)
To study user behavior, Google researchers ran a live experiment by dropping nearly 300 USB sticks around a university campus.
- Result: 48% were plugged in by unsuspecting students and staff.
- What users did: Many opened files on the drives despite no clear origin. Some even executed fake documents.
- Payloads (simulated): Non-malicious scripts logged activity for research purposes.
- Insight: Social engineering doesn’t need phishing emails just a believable prop and a curious target.
Case 3: Cracked Software Bait via Discord (2023–2024)
Cybercriminals shifted to platforms like Discord, Telegram, and Reddit to spread malware disguised as pirated software and “mod tools.”
- Modus operandi:
- Attackers uploaded cracked versions of games, video editors, or productivity apps.
- Distributed through private Discord servers and “free tools” websites.
- Once downloaded and executed, the software dropped RedLine Stealer or Lumma malware, scraping browser credentials and crypto wallets.
- Attackers uploaded cracked versions of games, video editors, or productivity apps.
- Victims: Primarily gamers, freelance creators, and developers seeking paid software for free.
- Takeaway: Baiting scaled to the masses and no USBs required.
Case 4: QR Code Baiting in the Wild (2025)
With QR codes embedded in everything from restaurant menus to parking systems, attackers have adapted baiting to the mobile-first world.
- The campaign: Rogue QR codes placed on posters and public ads in Europe redirected users to credential-harvesting sites disguised as login pages or app updates.
- Tech details:
- Domains mimicked Apple/Google update servers.
- Users were prompted to enter credentials or install malware APKs.
- Domains mimicked Apple/Google update servers.
- Notable feature: These baiting attacks bypassed email filters and antivirus entirely there was no file until after interaction.
- Victim base: Tourists, students, and commuters using QR codes in high-traffic zones.
Case 5: Internal Baiting During Red Team Engagements
Even cybersecurity professionals fall for the bait.
- Context: During a Red Team simulation for a Fortune 500 company, testers dropped USB sticks labeled “Executive Salaries 2025.xlsx” in break rooms.
- Outcome: Two employees plugged them in. One executed a macro-enabled Excel doc, which opened a reverse shell.
- Payload: A PowerShell-based implant gave attackers lateral movement across internal systems.
- Impact: Simulated data exfiltration within hours.
- Lesson: Baiting bypasses the firewall and jumps straight into your core network.
Why Baiting Still Works in 2025?

Despite years of security awareness training, endpoint protection platforms, AI-driven anomaly detection, and global cyber hygiene campaigns, baiting still thrives.
In fact, in 2025, it’s more dangerous, scalable, and effective than ever before. Why? Because baiting is not a technical exploit it’s a human exploit. And no patch can fix human behavior.
1. The Brain Is the Weakest Endpoint
Let’s start with the obvious: human psychology is static. While software evolves and systems get patched, the human OS remains vulnerable to the same old tricks.
- Curiosity: “What’s on this USB?”
- Greed: “Free software? Premium tools unlocked?”
- Urgency: “Your invoice is due download now!”
- Authority: “This job offer came from HR…”
Social engineers understand these cognitive triggers better than most psychologists. They don’t need zero-days when users will walk the payload in themselves. And baiting attacks prey directly on these predictable impulses.
2. AI Has Made Baiting Hyper-Personalized
Attackers in 2025 are no longer manually crafting fake lures they’re using AI to do it at scale:
- LLMs generate convincing job offer emails tailored to LinkedIn profiles.
- Voice clones simulate HR or tech support to add authenticity to USB drops or QR baits.
- AI-generated documents mimic internal formats, logos, and naming conventions.
- Automated payload generators obfuscate malware signatures in seconds, evading most heuristic detection tools.
What this means: Baiting is no longer generic, it’s bespoke, fast, and incredibly believable.
Read More On: How Do Macros Pose A Cybersecurity Risk?
3. Security Tools Still Can’t Fix User Behavior
You can deploy all the EDRs, SIEMs, and XDRs you want; none of them matter if the user willingly executes the payload.
- USB port blocking is often selectively enforced (exceptions made for “trusted” users or “urgent” scenarios).
- Endpoint controls are bypassed by signed payloads, LOLBins, or scripts abusing native Windows tools.
- Application whitelisting fails if users run code via PowerShell or script interpreters that appear legitimate.
Many baiting payloads are now fileless, abusing memory-resident execution via living-off-the-land binaries (e.g., mshta.exe, regsvr32.exe, rundll32.exe).
4. QR Codes: The New Bait Vector
The world is drowning in QR codes parking meters, restaurant menus, event check-ins, and ads. That ubiquity is now being weaponized.
- Quishing (QR phishing) has exploded in 2025, with rogue codes leading to credential theft, malware downloads, or spoofed login pages.
- QR baits can bypass traditional email scanning, since there are no attachments or clickable links just an image.
- Many mobile devices, especially Androids with sideloading enabled, are wide open to malicious APK installs from baited QR sources.
User trust in QR codes is dangerously high, making them an ideal bait vehicle.
5. Digital Fatigue Breeds Apathy
We live in a world of constant alerts, forced password resets, and mandatory training modules. The result? Security fatigue.
- Users are bombarded with security prompts they don’t fully understand.
- They begin to treat warnings as friction, not protection.
- In fast-paced environments, compliance takes a back seat to convenience.
This makes employees more susceptible than ever to simple bait tactics, especially when dressed up as routine business.
Read More On: 10 Online Best Dark Web Search Engines for Tor Browser
6. Baiting Requires No Exploit Chain
Most modern cyberattacks involve:
- Recon
- Exploit development
- Payload obfuscation
- Privilege escalation
- Lateral movement
Baiting shortcuts all of this. All the attacker needs is:
- A payload (which can be downloaded or run via USB)
- A lure (file, link, drive, QR)
- A human (to interact with it)
No exploit chain required. No shellcode needed. In many cases, no antivirus alert ever goes off. It’s clean, effective, and low-cost.
Read More On: NotEvil Search Engine: How It Works and What You Can Find
7. It Works Because It’s Still Underrated
Most organizations still focus on defending networks, not minds. Their spending goes toward:
- Cloud security
- SIEM logs
- Threat intel feeds
But baiting often bypasses these controls entirely by attacking the wetware the user sitting in the chair.
Red Teams know it. Hackers know it. Most CISOs know it too, but boards still want to see shiny dashboards, not cultural shifts.
Read More On: Top 10 Cybersecurity Forensic Tools For Ethical Hackers In 2025
How to Defend Against Baiting
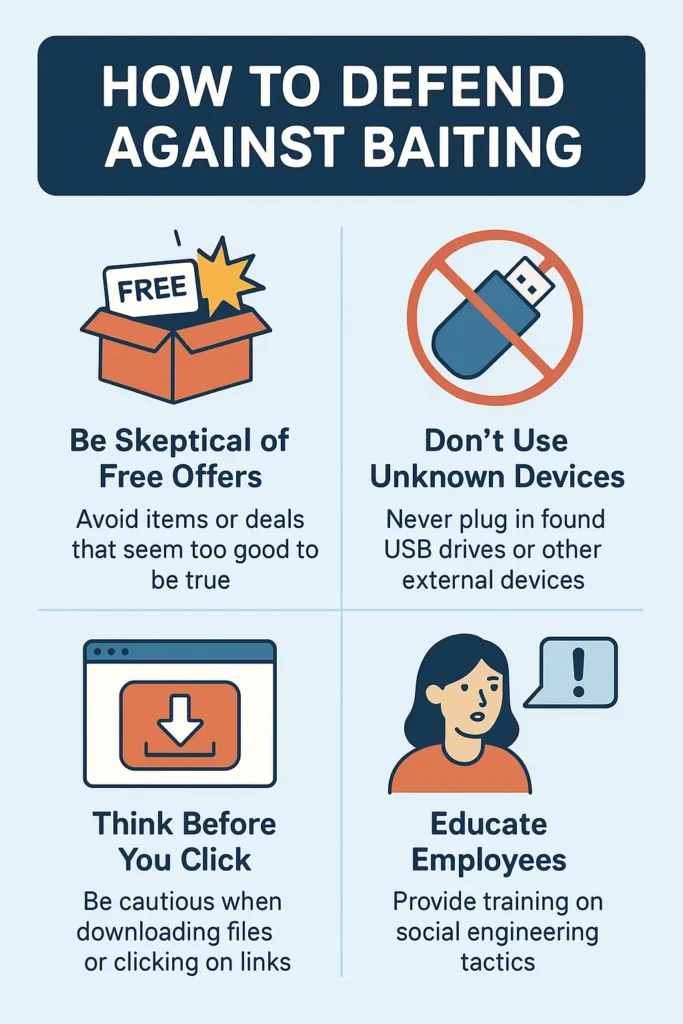
Defending against baiting requires more than antivirus software it demands a mix of technical controls, user awareness, and cultural resilience. Because baiting is a social engineering exploit, the best protection isn’t just code, it’s a mindset.
Below is a full-spectrum defense strategy split into two fronts: individual defense and organizational hardening.
Read More On: Which Of The Following Activities Poses The Greatest Personal Cybersecurity Risk?
A. For Individuals: Human Firewalls Start with You
Baiting targets you, not your system. Here’s how to lock yourself down.
1. Never Trust “Found” Tech
- Rule 1: If you find a USB drive, assume it’s bait. Don’t plug it in ever.
- If it’s work-related, report it to IT.
- For public events, consider all giveaway drives as potential threats.
2. Avoid Cracked Software and “Free” Tools
- Cracked installers, keygens, and pirated apps are prime bait vectors.
- Use trusted vendors or verified open-source tools.
- If the app isn’t digitally signed or comes from a sketchy site, don’t touch it.
3. Be Suspicious of QR Codes
- Avoid scanning random QR codes in public, on ads, or in unsolicited emails.
- Use apps that show the destination URL before launching the site.
- Prefer typing URLs manually or navigating through official apps.
4. Think Before You Click
- Slow down. Attackers thrive on impulse reactions.
- Hover over links, inspect downloads, and question anything that feels urgent, free, or too convenient.
- If in doubt, sandbox it or ask an expert.
5. Use Security Tools Smartly
- Enable real-time antivirus and anti-malware (Microsoft Defender + Malwarebytes = solid combo).
- Use browser extensions like uBlock Origin and NoScript to block drive-by downloads.
- On mobile, disable unknown source installs unless explicitly needed.
B. For Organizations: Build Systems That Assume Failure
Organizations need to operate on the assumption that someone, somewhere, will fall for the bait. Design your defenses accordingly.
1. Lock Down USB and Removable Media
- Use device control policies (via GPO, Intune, or MDM tools) to block unauthorized USB use.
- Allow only whitelisted hardware and log all connections.
- Consider USB data blocker devices or one-way write protections for approved usage.
2. Train Like It’s the Real Thing
- Ditch the boring PowerPoint training. Use live baiting simulations in red team drills.
- Teach users how baiting works with real examples, not hypotheticals.
- Focus on behavioral reinforcement: curiosity kills networks.
3. Endpoint Hardening & Threat Detection
- Use EDR/XDR platforms that detect LOLBins, script abuse, and unauthorized app launches.
- Sandbox or block .LNK, .HTA, .JS, and macro-enabled files by default.
- Monitor USB activity, anomalous file execution, and outbound traffic patterns.
4. Apply the Principle of Least Privilege
- Users should not run with admin rights unless necessary.
- Restrict script execution via AppLocker or WDAC (Windows Defender Application Control).
- Use virtualization or disposable VMs for testing untrusted files.
5. Establish Incident Response for Baiting Scenarios
- Have a playbook ready: What happens if someone plugs in a rogue USB or installs suspicious software?
- Include baiting in phishing and malware response plans.
- Build automated alerts for signs of persistence techniques commonly used in baiting (registry edits, task schedulers, etc.).
Advanced Defenses (Optional but Recommended)
- USB honeytokens: Drop decoy USBs with tracking payloads to monitor unauthorized usage.
- Deception tech: Use honeypots or endpoint decoys to catch bait-triggered activity in real time.
- Zero Trust frameworks: Ensure that every device, user, and action is verified, not assumed.
Culture Is the Ultimate Firewall
No technical control can replace a security-minded culture. Encourage users to be paranoid (in a good way), reward caution, and make it easy to report suspicious activity without fear of blame.
Baiting works when people aren’t paying attention. Your job is to make sure they always are.
Read More On: The Role of ZTNA and VPN in Modern Cybersecurity Strategies
Hacker Insight: Why Baiting Will Never Die

You can patch an OS. You can segment a network. You can even drop seven figures on a shiny SIEM platform. But you can’t patch the human brain.
And that’s why baiting the simplest, dirtiest, and most elegant social engineering tactic in the book will never die.
For those who operate in the margins of digital society Red Teamers, social engineers, black hats, and gray hats baiting remains a go-to weapon. Not because it’s cutting-edge. But because it works. Always has. Always will.
Read More On : Cybersecurity YouTube Channels: Top 10 You Must Follow [2025]
Humans: The Eternal Zero-Day
Every infosec veteran knows this truth: humans are the ultimate legacy system. Their cognitive biases are ancient. Their instincts are exploitable. They click before they think.
- Curiosity says: “What’s on this USB?”
- Greed whispers, “This cracked tool will save me hundreds.”
- Urgency yells: “Download this file before the offer expires!”
These aren’t bugs. Their features hardcoded into our neural firmware. That’s why baiting endures. No matter how modern the stack or hardened the system, humans remain socially hackable.
The Appeal of Low-Tech, High-Yield Attacks
Baiting isn’t about elite code. It’s about tactical manipulation. A flash drive and a sharp mind can breach targets that a buffer overflow never will.
- A $10 Rubber Ducky, preloaded with HID scripts, will drop a payload faster than any exploit kit.
- A QR sticker on a Starbucks ad can hijack mobile sessions with zero friction.
- A fake job offer on LinkedIn, bundled with a macro-laced resume, can land inside the C-suite.
Baiting strips hacking down to its purest form minimal code, maximum psychological pressure.
Use Our Cybersecurity Risk Calculator
Defensive Evolution Creates Offensive Gaps
The more defensive tools evolve, the more baiting thrives in the blind spots.
- Firewalls don’t matter when the threat enters via USB.
- EDRs can’t stop users from executing whitelisted malware-laced documents.
- DLP tools fail when a user willingly enters credentials into a fake form.
Even in air-gapped environments, history proves attackers don’t need remote exploits they just need an unthinking moment of trust. Baiting is the offline pivot point that can breach otherwise impenetrable systems.
Read More On: Is Cybersecurity a Good Career in 2025?
Baiting Is Hacker Culture at Its Core
To hackers, especially those raised on IRC, DEF CON, and /r/netsec, baiting isn’t just a tactic. It’s a mindset.
It’s the con before the code. The psych game before the payload. A flex of creativity over raw compute.
In Red Team channels, pulling off a bait op that leads to full domain compromise is treated with more respect than popping a box with Metasploit. It says: “I played the human, not just the system.”
Baiting captures the original spirit of hacking: understanding how things and people work, then bending them to your will.
Read More On: Which Of The Following Is Not A Function Of A Cybersecurity Framework?
Baiting Scales Infinitely, Costs Practically Nothing
Unlike technical exploits that require:
- Research
- Development
- Custom payloads
- Expensive infrastructure
Baiting is infinitely scalable. One lure can hit hundreds. One cracked app can infect thousands. One QR code can phish an entire event crowd.
For attackers, it’s dirt cheap. For defenders, it’s hellishly unpredictable. That asymmetry is the reason that baiting will outlive most cybersecurity trends.
Read More On: How Can Generative AI Be Used In Cybersecurity
In an Over-Engineered World, Simple Still Wins
The cybersecurity industry is addicted to complex threat graphs, AI-driven anomaly detection, and blockchain logging. But every additional layer gives users more to ignore, bypass, or misinterpret.
Baiting cuts through all of it like a lockpick through a screen door.
- No zero-day.
- No malware signature.
- Just a simple action, and human failure delivers the rest.
Final Thoughts
So, what is baiting in cyber security?
It’s not just a relic of early hacker culture, it’s a living, breathing threat that thrives in modern digital ecosystems.
From fake QR codes to rogue USBs and AI-crafted lures, baiting has evolved, but its core strategy remains unchanged: to exploit human nature.
In an age of multi-million-dollar cybersecurity budgets and AI-enhanced defense tools, it’s ironic that one of the most effective attack vectors is still a simple piece of bait and a curious click.
Baiting works because it doesn’t need to outsmart machines it only needs to outmaneuver people. And until the culture around trust, urgency, and convenience is reprogrammed, baiting will remain one of the most enduring tactics in the hacker playbook.
If there’s one lesson to take away from this, stay skeptical, stay alert, and remember in cybersecurity, the most dangerous vulnerability often sits behind the keyboard.
Frequently Asked Questions
How does baiting differ from phishing?
While both are social engineering attacks, phishing typically involves emails or fake websites to steal credentials, whereas baiting uses physical or digital “bait” like a USB drive or pirated software to deliver a malicious payload when the victim interacts with it.
Can baiting be used against organizations?
Absolutely. Red Teams and real-world attackers often use baiting to breach corporate networks by planting rogue USBs or distributing fake job files. Even air-gapped systems have been compromised this way, as seen in the Stuxnet incident.
Is baiting considered a cybercrime?
Yes. Deploying baiting attacks is illegal under most cybersecurity laws. It’s classified as unauthorized access, malware distribution, or fraud, depending on the method and intent. Legal Red Team simulations are the only ethical use of this approach.
What is spoofing in cyber security?
Spoofing in cyber security refers to a technique where attackers disguise themselves as a trusted person or system to deceive victims. This can involve faking emails, IP addresses, websites, or communications to trick users into revealing sensitive data or granting access.
What is a backdoor in cyber security?
A backdoor is a hidden method of bypassing normal security controls to gain access to a system or network. It can be intentionally built-in for legitimate purposes or secretly installed by attackers, allowing them to enter undetected and avoid standard authentication measures.