Which of the following is not a function of a cybersecurity framework?
A cybersecurity framework typically includes five core functions: Identify, Protect, Detect, Respond, and Recover. These are designed to help organizations manage cyber risk effectively. However, functions like “guaranteeing 100% security” or “eliminating all risk” are not part of any cybersecurity framework, because no framework can offer absolute protection from evolving threats.
Cybersecurity frameworks are essential tools that help organizations prepare for, respond to, and recover from cyber threats.
Whether you’re studying for a certification like CISSP or Security+, or simply want to better understand how digital defenses work, it’s important to know exactly what these frameworks do — and what they don’t.
In this article, we’ll break down:
- The core functions of cybersecurity frameworks,
- The common misconceptions, and
- The definitive answer to:
Which of the following is not a function of a cybersecurity framework?
What Is a Cybersecurity Framework?
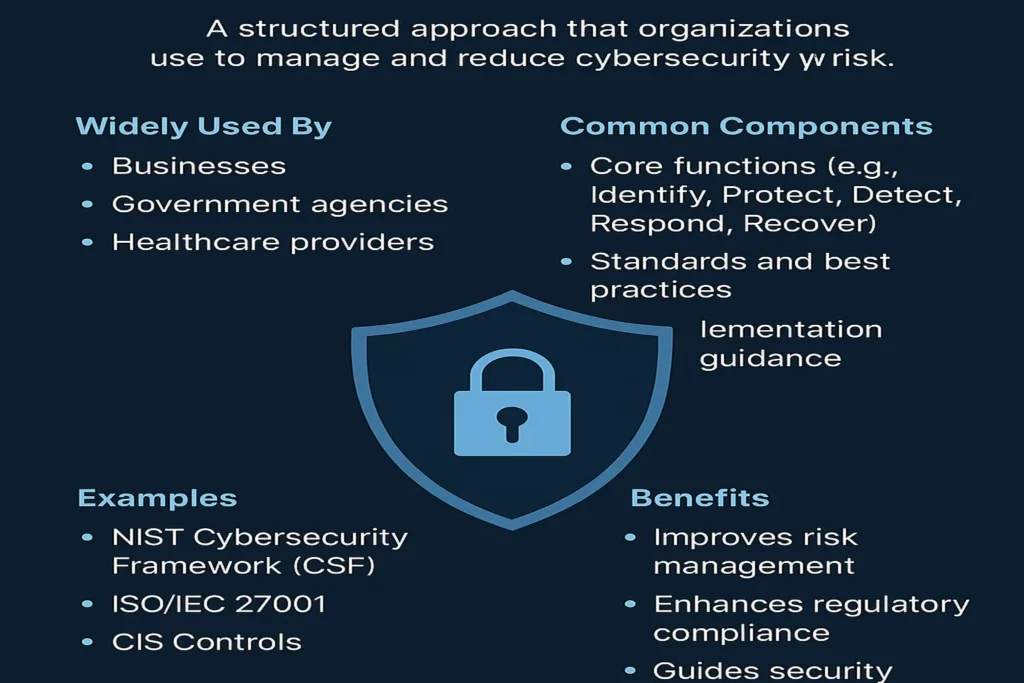
A cybersecurity framework is a structured set of guidelines and best practices used to manage and reduce cyber risk.
It helps organizations protect their information systems by defining processes for identifying threats, securing assets, detecting incidents, responding effectively, and recovering quickly.
Most frameworks are built around five key functions: Identify, Protect, Detect, Respond, and Recover. These functions guide the development of security strategies that are measurable, repeatable, and aligned with business goals.
Popular examples include:
- NIST Cybersecurity Framework (CSF) – widely used in the U.S. for aligning IT security with risk management.
- ISO/IEC 27001 – an international standard for managing information security.
- CIS Controls – a prioritized set of defensive actions for reducing the most common attack vectors.
Implementing a cybersecurity framework helps organizations stay compliant, improve resilience, and respond more effectively to cyber threats.
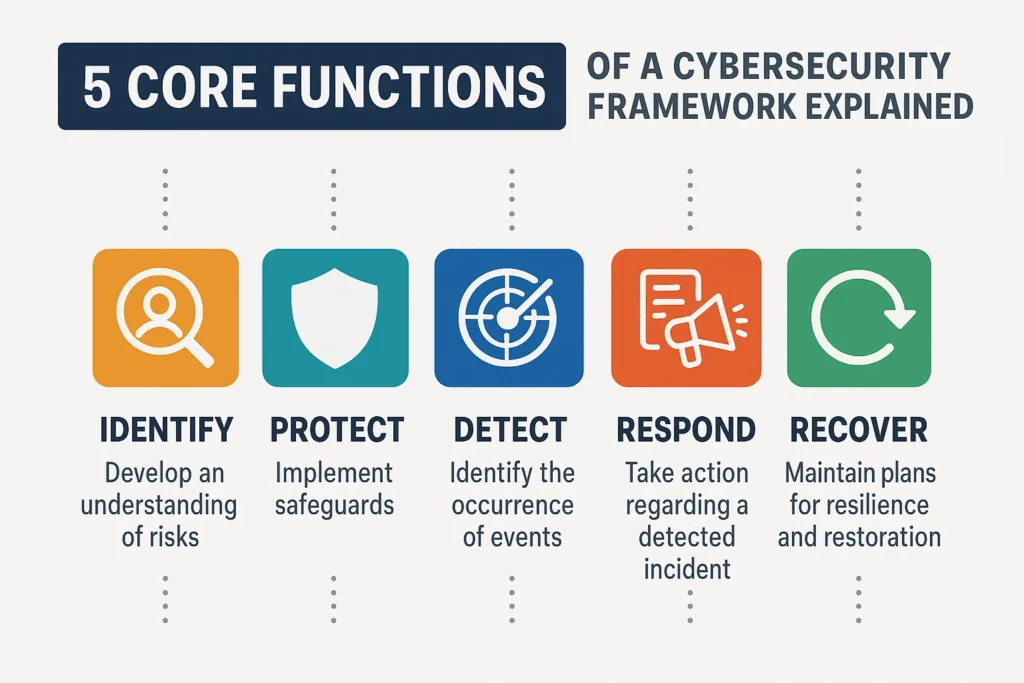
5 Core Functions of a Cybersecurity Framework Explained
| Function | Description | Key Components | Technical Details |
| Identify | Develop an organizational understanding of cybersecurity risk to systems, people, assets, data, and capabilities. | Asset Management, Business Environment, Governance, Risk Assessment, Risk Management Strategy, Supply Chain Risk Management | Includes mapping digital assets, identifying system dependencies, and evaluating supply chain risks. |
| Protect | Implement appropriate safeguards to ensure the delivery of critical infrastructure services and limit or contain cybersecurity events. | Access Control, Awareness and Training, Data Security, Information Protection Processes, Maintenance, Protective Technology | Enforces authentication policies, encryption standards, user privilege management, and secure software configurations. |
| Detect | Define the activities to identify the occurrence of a cybersecurity event in a timely manner through continuous monitoring and detection processes. | Anomalies and Events, Security Continuous Monitoring, Detection Processes | Utilizes SIEM systems, anomaly detection, and real-time log correlation for threat visibility. |
| Respond | Develop and implement appropriate response activities to contain the impact of a cybersecurity incident and support recovery efforts. | Response Planning, Communications, Analysis, Mitigation, Improvements | Involves executing predefined playbooks, communicating with stakeholders, and performing root cause analysis. |
| Recover | Develop and implement activities to maintain resilience and restore capabilities or services impaired by a cybersecurity incident. | Recovery Planning, Improvements, Communications | Focuses on service restoration, system revalidation, and post-incident review to strengthen future response. |
A robust cybersecurity framework is typically structured around five core functions that guide how organizations manage and mitigate cybersecurity risk.
These functions, defined in the widely adopted NIST Cybersecurity Framework (CSF), represent a lifecycle approach to threat management.
They are not meant to be linear but rather continuous and adaptive to an evolving threat landscape.
Understanding these five pillars is essential for developing a resilient and compliant cybersecurity program.
Each function encapsulates specific goals, technical processes, and operational practices necessary to defend systems and data against cyber threats.
1. Identify
The Identify function focuses on developing an understanding of the organization’s environment to manage cybersecurity risk. This includes identifying critical assets, business processes, third-party dependencies, and associated vulnerabilities.
Key activities include:
- Inventory of hardware and software assets
- Risk assessments and threat modeling
- Mapping to business context and compliance requirements
- Establishing governance and roles
This function sets the foundation for all other security measures. Without knowing what you’re protecting, no defense strategy can be effective.
2. Protect
The Protect function involves deploying appropriate safeguards to ensure the continued delivery of critical infrastructure services. It aims to limit or contain the impact of a potential cybersecurity event.
Key activities include:
- Access control and identity management
- Data encryption and protection technologies
- Endpoint and application security
- Secure configuration and patch management
- User awareness and security training
These are the proactive controls that help minimize the attack surface and reduce exploitation opportunities.
3. Detect
Detect ensures that organizations can recognize cybersecurity events promptly. Continuous monitoring and anomaly detection are central to this function.
Key activities include:
- Security Information and Event Management (SIEM)
- Intrusion Detection Systems (IDS)
- Threat intelligence integration
- Behavioral analytics and anomaly detection
Early detection helps reduce the dwell time of attackers and limits the impact of breaches.
4. Respond
The Respond function defines the steps taken once a cybersecurity incident is detected. It focuses on containment, analysis, eradication, and communication.
Key activities include:
- Incident response planning and execution
- Threat containment and forensic analysis
- Public and internal communications
- Lessons learned and root cause analysis
Having a documented incident response plan is critical for reducing recovery time and reputational damage.
5. Recover
The Recover function ensures the organization can restore services and capabilities after a cybersecurity incident. It also supports resilience by implementing improvements based on lessons learned.
Key activities include:
- Disaster recovery and business continuity planning
- System backups and restoration
- Post-incident reviews and strategic improvements
Effective recovery reduces downtime, maintains trust, and helps prepare for future threats.
These five core functions provide a systematic and repeatable approach to securing systems and data.
By implementing them using proven standards and tools, such as NIST SP 800-30, ISO 27001, Splunk, SOAR platforms, and DR solutions, organizations can develop a cybersecurity program that’s not only compliant but also resilient and future-proof.
Which of the Following Is NOT a Function of a Cybersecurity Framework?

A cybersecurity framework provides a strategic structure for managing cyber risk, aligning security practices with business objectives, and maintaining operational resilience.
Frameworks like NIST CSF, ISO/IEC 27001, and CIS Controls define core functions—Identify, Protect, Detect, Respond, and Recover—that support a lifecycle-based approach to securing critical infrastructure and data assets.
However, it’s important to understand what falls outside the scope of a cybersecurity framework.
Not a Function of a Cybersecurity Framework:
“Eliminating all cyber risk” is not a function of any cybersecurity framework.
Cybersecurity frameworks are risk-based, meaning they focus on reducing risk to acceptable levels, not achieving zero risk, which is unrealistic and technically unachievable. Frameworks do not:
- Guarantee absolute protection
- Prescribe specific tools (e.g., antivirus software)
- Eliminate all vulnerabilities
- Ensure compliance without organizational implementation
Core Intent of a Cybersecurity Framework
Frameworks are designed to:
- Establish governance and risk assessment processes
- Support threat detection, incident response, and recovery planning
- Guide the implementation of technical and administrative controls
- Improve organizational security maturity over time
- Align with compliance frameworks like HIPAA, GDPR, or FISMA
Correct Answer:
Eliminating all cyber risk is NOT a function of a cybersecurity framework.
Instead, frameworks support continuous improvement, risk mitigation, and resilience-building, not total security elimination.
Examples of Popular Cybersecurity Frameworks (NIST, ISO, CIS)

| Framework | Developed By | Primary Focus | Structure | Common Use Cases | Certification Available | Technical Details |
| NIST CSF | NIST (U.S. Government) | Risk-based approach to cybersecurity with flexible implementation tiers | 5 core functions (Identify, Protect, Detect, Respond, Recover) and implementation tiers | Government, healthcare, and financial institutions for alignment and risk governance | No (but widely adopted as a standard) | Uses a risk-based methodology with tiered maturity levels. Often integrated into enterprise security governance. Commonly mapped to CIS Controls or ISO standards. |
| ISO/IEC 27001 | International Organization for Standardization (ISO) & IEC | Establishing and maintaining an auditable Information Security Management System (ISMS) | Annex A controls mapped to risk assessments and management processes | Global enterprises and SaaS providers seeking certification and compliance | Yes (ISO 27001 certification available through audit) | Requires a documented ISMS, internal audits, management review, and continuous improvement. Provides certification through accredited bodies. |
| CIS Controls | Center for Internet Security (CIS) | Prioritized set of actionable controls for defending against known cyber threats | 18 controls grouped into implementation groups (IG1, IG2, IG3) | SMBs and IT teams needing tactical, practical security implementation | No (used as best-practice guidelines) | Designed to be easily implemented. Controls are highly prescriptive and practical for immediate impact. Divided into IG1 (basic), IG2 (intermediate), IG3 (advanced). |
Cybersecurity frameworks provide standardized methods for identifying, managing, and reducing cyber risk.
Depending on an organization’s industry, size, or compliance needs, different frameworks may be adopted. Below are three of the most widely used and respected cybersecurity frameworks globally:
1. NIST Cybersecurity Framework (CSF)
Developed by the National Institute of Standards and Technology (NIST), the NIST CSF is a voluntary framework primarily used in critical infrastructure sectors but is applicable across industries.
Key Highlights:
- Based on 5 core functions: Identify, Protect, Detect, Respond, Recover
- Provides implementation tiers and categories for maturity mapping
- Supports risk-based decision making
Used by: Government agencies, healthcare providers, financial institutions, and enterprises aiming for risk alignment and regulatory compliance.
2. ISO/IEC 27001
The ISO/IEC 27001 is an international standard for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS).
Key Highlights:
- Focuses on risk assessment, control objectives, and continual improvement
- Requires documentation and top-level management buy-in
- Auditable for ISO certification
Used by: Multinational corporations, tech firms, and SaaS companies needing global compliance and security certification.
3. CIS Critical Security Controls
The CIS Controls, published by the Center for Internet Security, are a set of 18 prioritized and actionable controls designed to mitigate the most common cyber threats.
Key Highlights:
- Tactical and implementation-focused
- Frequently updated to reflect real-world attack patterns
- Easily mapped to NIST, ISO, and other frameworks
Used by: SMBs, IT service providers, and organizations seeking rapid hardening of their security posture.
Choosing the Right Framework
Each of these frameworks can be used independently or integrated together, depending on your organization’s risk profile and compliance obligations. For example:
- A company may use NIST CSF for structure,
- Implement ISO 27001 for certification.
- And adopt CIS Controls for day-to-day operational security.
Why Understanding Framework Functions Matters for Cyber Risk Management?
Cyber risk is no longer just an IT problem — it’s a business risk that affects operational continuity, data integrity, regulatory compliance, and customer trust.
That’s why organizations across industries are turning to cybersecurity frameworks to build structured, repeatable, and risk-aware security programs. And yet, many professionals still ask: Which of the following is not a function of a cybersecurity framework? Understanding the answer to that question is essential for separating strategic cybersecurity objectives from unrealistic expectations.
Grasping the five core functions of cybersecurity frameworks — Identify, Protect, Detect, Respond, and Recover — is critical for aligning security initiatives with business priorities and improving an organization’s overall risk posture.
1. Transforms Cybersecurity from Reactive to Proactive
Many organizations operate in a reactive mode, responding only after a breach. Framework functions like Identify and Protect allow security teams to preemptively discover vulnerabilities, assess threats, and implement technical and administrative controls before damage occurs.
Example: A manufacturing company using NIST CSF can identify legacy OT (Operational Technology) systems and apply protections to prevent ransomware infections.
2. Supports Quantifiable Risk Management
Cybersecurity frameworks promote a risk-based approach, enabling teams to prioritize mitigation efforts based on the likelihood and impact of different threats.
Understanding how each function contributes to risk reduction — especially Detect and Respond — helps CISOs make informed decisions on resource allocation, tooling, and process maturity.
Example: A financial firm may prioritize email filtering and SIEM investment to enhance detection after identifying phishing as a high-risk attack vector.
3. Enables Strategic Compliance Alignment
Frameworks serve as a blueprint for complying with regulations like GDPR, HIPAA, FISMA, and PCI-DSS. By mastering the underlying functions, teams can map controls directly to regulatory requirements, streamlining audit processes and reducing compliance gaps.
Example: ISO/IEC 27001 compliance requires an ISMS, which aligns directly with the Identify and Protect functions.
4. Improves Incident Preparedness and Response Time
Knowing how the Respond and Recover functions operate allows teams to build and test incident response playbooks, reduce downtime, and execute disaster recovery with precision.
Organizations that understand and apply these functions typically:
- Contain breaches faster
- Reduce legal liability
- Protect brand reputation
5. Drives Continuous Improvement Through Resilience
Cybersecurity isn’t a one-time project — it’s a continuous lifecycle. Framework functions emphasize continuous monitoring, improvement, and adaptation, especially through post-incident reviews (Recover) and evolving risk landscapes (Identify).
Example: After a breach, an organization uses lessons learned to update its asset inventory, risk model, and controls, effectively strengthening its entire security ecosystem.
In short, Understanding framework functions empowers organizations to treat cybersecurity as a strategic asset, not just a technical necessity. It ensures that security investments align with actual risk, support compliance, and build long-term digital resilience.
Cybersecurity Framework Quiz: Can You Identify the Right Functions?
Understanding the five core functions of a cybersecurity framework — Identify, Protect, Detect, Respond, and Recover — is essential for implementing a risk-based security strategy that aligns with widely adopted frameworks like NIST CSF and ISO/IEC 27001.
Each function plays a specific role in the cybersecurity lifecycle: from asset inventory and risk analysis (Identify), to access control and encryption (Protect), ongoing threat detection (Detect), incident containment (Respond), and restoring business operations (Recover).
Yet, despite their strategic importance, these high-level functions are often misunderstood or confused with tactical tools like firewalls or antivirus software.
A common misconception—especially among exam candidates—is the belief that a cybersecurity framework can eliminate all cyber risks.
This leads to one of the most frequently asked questions in training: Which of the following is not a function of a cybersecurity framework? Understanding the correct answer is key to grasping the true intent and scope of these frameworks.
That’s why taking a structured cybersecurity framework quiz can help reinforce foundational concepts, dispel myths, and ensure your knowledge aligns with real-world standards.
Whether you’re studying for a certification exam like CISSP, Security+, or simply want to improve your operational readiness, this quiz will challenge your ability to:
- Map real-world scenarios to the correct framework function
- Distinguish between strategic and tactical responsibilities
- Understand how these functions interact across the security lifecycle
By mastering the functional roles within cybersecurity frameworks, you’ll not only improve your exam performance but you’ll also strengthen your organization’s cyber resilience and compliance posture.
Cybersecurity Framework Quiz: Can You Identify the Right Functions?
Test your knowledge of the five core cybersecurity framework functions: Identify, Protect, Detect, Respond, and Recover.
Question 1:
A company inventories all digital assets and evaluates third-party vendor risks.
Which function does this represent?
- A) Protect
- B) Identify
- C) Detect
- D) Recover
Reveal Answer ✅ Correct Answer: B) Identify
This function focuses on asset management, risk assessments, and supply chain risk evaluation.
Question 2:
The IT team implements multi-factor authentication and encrypts sensitive customer data.
Which function is this?
- A) Detect
- B) Respond
- C) Protect
- D) Identify
Reveal Answer ✅ Correct Answer: C) Protect
Protect includes access controls, data security, and safeguarding critical infrastructure.
Question 3:
The security team uses a SIEM to analyze logs and alert on suspicious login patterns.
Which function is most aligned?
- A) Detect
- B) Respond
- C) Recover
- D) Identify
Reveal Answer ✅ Correct Answer: A) Detect
Detect covers real-time threat monitoring and anomaly detection capabilities.
Question 4:
After a phishing incident, the team follows an incident response plan and notifies stakeholders.
Which function is this?
- A) Recover
- B) Respond
- C) Protect
- D) Identify
Reveal Answer ✅ Correct Answer: B) Respond
Respond includes mitigation, analysis, communication, and containment of incidents.
Question 5:
The company restores operations from backups and performs a post-incident review.
Which function does this fall under?
- A) Detect
- B) Identify
- C) Protect
- D) Recover
Reveal Answer ✅ Correct Answer: D) Recover
Recover focuses on service restoration, learning from incidents, and ensuring resilience.
Total Your Score:
- 5/5: Framework Expert
- 3–4/5: Strong Knowledge — just refine a few areas!
- 1–2/5: Time to review the core framework functions.
Want to assess your real-world exposure?
Take our Cybersecurity Risk Calculator for actionable insights tailored to your threat landscape.
Resources to Learn More About Cybersecurity Frameworks
If you’re serious about building a secure infrastructure or preparing for a certification like CISSP, relying on trusted and up-to-date resources is essential.
Below are the best places to learn about cybersecurity frameworks, including NIST CSF, ISO/IEC 27001, and CIS Controls.—all of which are built around risk-based, strategic functions.
A common question that arises, especially in certification prep, is: Which of the following is not a function of a cybersecurity framework? Understanding the answer to this helps distinguish core principles from common misconceptions.
The official NIST Cybersecurity Framework site is the go-to source for understanding the five core functions — Identify, Protect, Detect, Respond, and Recover. It offers detailed guidance, implementation tiers, and real-world examples for businesses of all sizes.
For those focused on international compliance and enterprise-level security, the ISO/IEC 27001 standard provides a comprehensive approach to building and maintaining an Information Security Management System (ISMS). It’s one of the most recognized cybersecurity standards worldwide.
If you’re looking for practical, prioritized defensive measures, the CIS Controls v8 offers 18 actionable controls designed to stop the most common cyber attacks.
These are highly effective for small businesses and IT teams seeking tactical implementation.
To gain deeper insights and credentials, certifications like CISSP and CompTIA Security+ include in-depth coverage of these frameworks.
Meanwhile, the NIST Online Learning Series provides free video training directly from the source.
Use our free Cybersecurity Risk Calculator to assess your current risk level and receive practical steps aligned with NIST and ISO frameworks.
And if you want to compare how NIST, ISO, and CIS align, use framework mapping tools to explore cross-framework compatibility.
By leveraging these resources, you’ll stay aligned with industry standards, improve your risk management posture, and build a resilient cybersecurity strategy that scales with your needs.
Final Thoughts
Understanding the core functions of a cybersecurity framework—Identify, Protect, Detect, Respond, and Recover—is essential for organizations aiming to manage cyber risk effectively.
These structured functions provide a foundation for proactive security, regulatory compliance, and operational resilience.
However, it’s equally important to understand what cybersecurity frameworks are not designed to do. That’s why questions like “Which of the following is not a function of a cybersecurity framework?” are commonly featured in security certifications and technical assessments.
The correct answer—eliminating all risk—highlights a critical truth: no framework can guarantee complete protection. Instead, these frameworks offer a systematic approach to reducing risk to an acceptable level.
If you’re ready to apply this knowledge in a practical context, head over to CyberLad.io and use our free Cybersecurity Risk Calculator to evaluate your organization’s risk profile.
You’ll receive actionable insights based on core framework principles—so you can move from understanding to implementation.
Frequently Asked Questions
What Are the 5 Types of Cybersecurity?
The five primary areas of cybersecurity include network security, application security, information security, operational security, and disaster recovery/business continuity. These domains work together to protect digital assets from unauthorized access, data breaches, and cyber threats.
What Are the 6 Types of Cybersecurity?
Cybersecurity can be categorized into six major types:
- Network Security
- Application Security
- Information (Data) Security
- Cloud Security
- IoT (Internet of Things) Security
- Identity and Access Management (IAM)
These layers of defense are essential for safeguarding systems, data, and users across modern digital infrastructures.
What Are the 3 Components of the Cybersecurity Framework?
The Cybersecurity Framework, particularly the NIST CSF, is built around three core components:
- Framework Core – The five key security functions: Identify, Protect, Detect, Respond, Recover
- Implementation Tiers – Levels of cybersecurity maturity and risk management
Profiles – Customized alignment of framework functions to business goals and risk tolerance
What Are Three Functions of a Cybersecurity Framework?
While the full NIST framework outlines five functions, three of the most central are:
- Identify – Understand assets, risks, and vulnerabilities
- Protect – Implement safeguards to reduce the risk of cyber incidents
- Detect – Monitor systems to identify security events in real time
These form the foundation for building a risk-based and proactive cybersecurity strategy.
What Are the 4 P’s of Cybersecurity?
The “4 P’s of Cybersecurity” refer to a holistic framework focused on:
- Planning – Strategic preparation and risk assessment
- Prevention – Proactive threat mitigation
- Protection – Technical controls and policy enforcement
- Privacy – Data governance and regulatory compliance
This approach ensures that organizations address both technical and policy-driven aspects of cybersecurity.
What Is Cyber 4?
Cyber 4+ is an educational pathway that allows high school students to earn four CompTIA cybersecurity certifications and an associate degree during their first year of college, at no cost. It combines dual enrollment and career and technical education (CTE) to fast-track cybersecurity careers for youth.
Related Articles:
NotEvil Search Engine: How It Works and What You Can Find






